DEFRAY – Ransomware hitting Healthcare and Education Organizations
After the world wide attack of WannaCry ransomware, hackers are putting a lot of effort into developing higher levels of ransomware. A new wave of ransomware attack has begun targeting Healthcare and Educational Organizations spreading via E-Mails…
After the world wide attack of WannaCry ransomware, hackers are putting a lot of effort into developing higher levels of ransomware. A new wave of ransomware attack has begun targeting Healthcare and Educational Organizations spreading via E-Mails with carefully designed social engineering methods.
What is DEFRAY?
This threat was recently analyzed by the researchers at proofpoint. The name DEFRAY was given to the malware because of the name of Command and Control (C&C) server hostname from the first observed attack: defrayable-listings[.]000webhostapp[.]com
How does DEFRAY attack Work?
These ransomware are spread in Microsoft Word document attachments containing an embedded executable (specifically, an OLE packager shell object) in email. Below images are screenshots of some sample attachments that contains this Ransomeware.
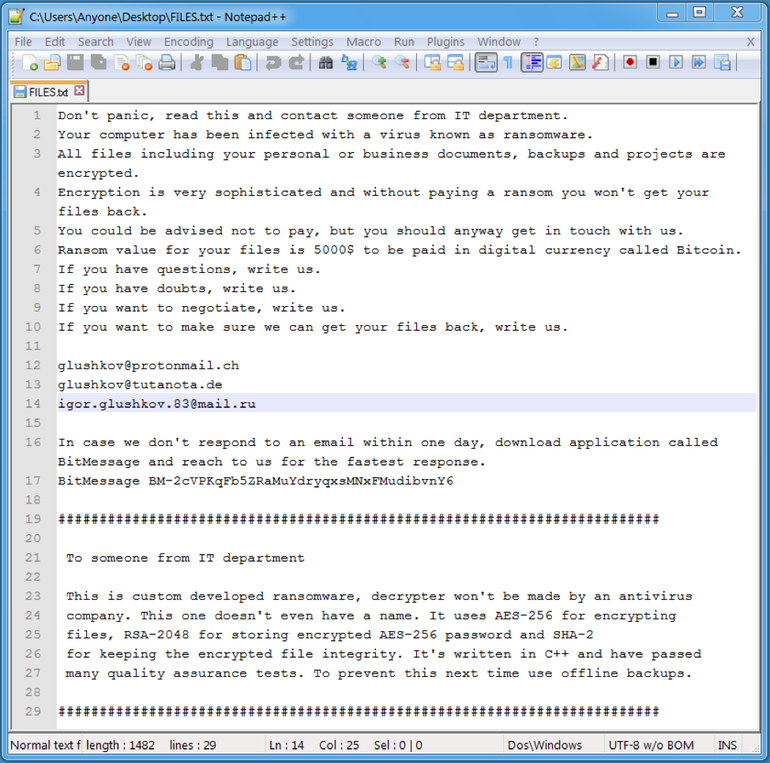
If the victim clicks on the embedded executable, ransomware is copied in a name such as taskmgr.exe or explorer.exe in the %TMP% folder and executed. If the ransomware is executed, all the data is encrypted and rendered useless to the victim . To make sure that the user understand what was just happened, files in the name “HELP.txt” or “FILES.txt” are generated through out the folders of the system. They are demanding $5000 from infected victims in exchange for their data.
Infected OS
Currently, this infection is reported in windows machine only. However, the effects are different in different windows OS. On Windows 7 the ransomware monitors and kills running programs with a GUI, such as the task manager and browsers. We have not observed the same behavior on Windows XP.
How not to be Victim?
This ransomware uses the old fashioned Social Engineering method of making the victim click and download malicious file from an E-Mail. So never click on any suspicious links or thumbnails in the mail without verifying it. In the note, it was also mentioned that it is a custom developed ransomware and decrypters wont be made by any antivirus company. However, it is always a good idea to keep your Firewall and anti Malware software uptodate.


![[Solved] Unable to locate package linux-headers | How to Install Kali 2020 Headers | Install Virtual Box](https://hackersgrid.com/wp-content/uploads/2017/08/kali-wallpaper-2015-v1.1.0-1.jpg)

