BeEF Attack Outside the LAN with 2048 Game
In the previous posts, I told you everything about BeEF, BeEF hook and showed how to create a malicious HTML game with BeEF hook script, port forwarding in router and how to setup NOIP Dynamic DNS Service…
In the previous posts, I told you everything about BeEF, BeEF hook and showed how to create a malicious HTML game with BeEF hook script, port forwarding in router and how to setup NOIP Dynamic DNS Service in Kali Linux. Now let us combine everything and perform a real attack using BeEF outside the LAN with a little bit of social engineering
In this tutorial, we are going to take this BeEF attack outside the LAN. I will also show you how to access BeEF control panel from outside our network.
What do we have in hand?
- We have BeEF. Click here to install if you dont have it installed.
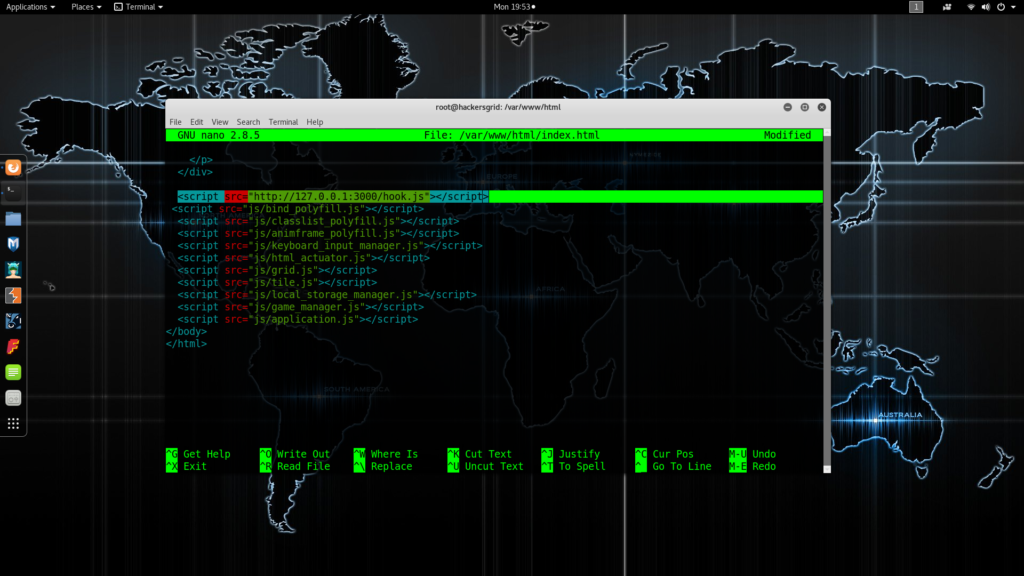
- A HTML Game with BeEF hook in it. Click here to setup a Web page.
- Port Forwarded (80) Router. Click here to know how to port forward.
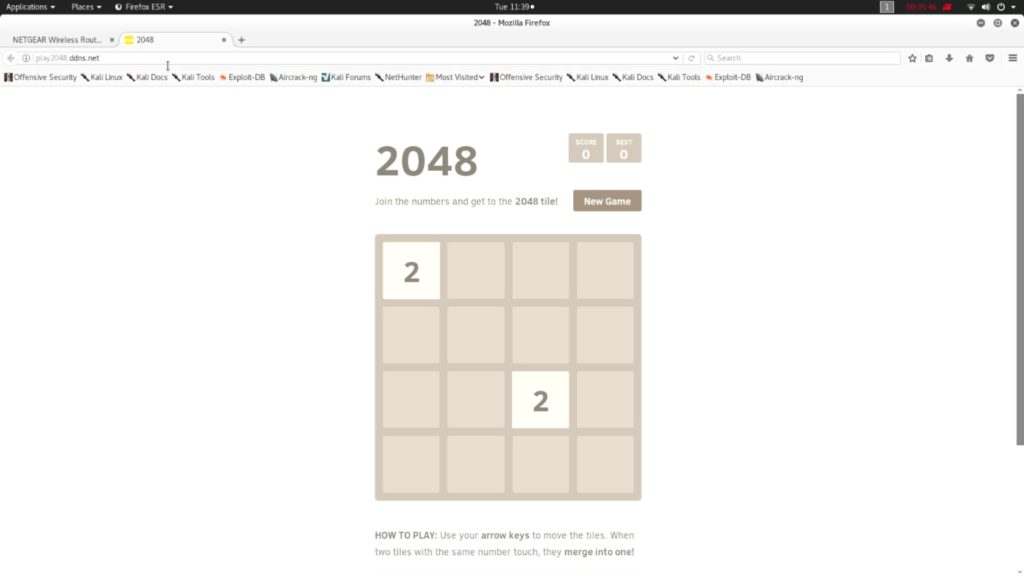
- A NOIP hostname (play2048.ddns.net). Click here to set up NOIP.
Before proceeding make sure that you have all these things ready with you.
What we are going to do is, we will set up a server (I am using my Raspberry Pi) which will host the HTML game 2048 with BeEF hook in it. We also setup a NOIP DUC running in it so that it will map the public IP with our hostname (play2048.ddns.net). In order to redirect port 80 traffic from router to Raspberry Pi, we will add a port forwarding rule in the router.
When someone click on our hostname, or if someone type it in the URL, he will be redirected to my router, from where it will be forwarded to my raspberry pi which will serve the malicious webpage. This hooked browser can be viewed and controlled from BeEF control panel which can be accessed outside the network where the server is running.
Let us Start
Video Tutorial
Setting up Webpage
As mentioned in my previous post, first thing you need is a webpage with BeEF hook script in it. Click here for detailed instructions. Start apache webserver and try to access the webpage by issuing your IP address or 127.0.0.1 (if you are trying from the same machine).
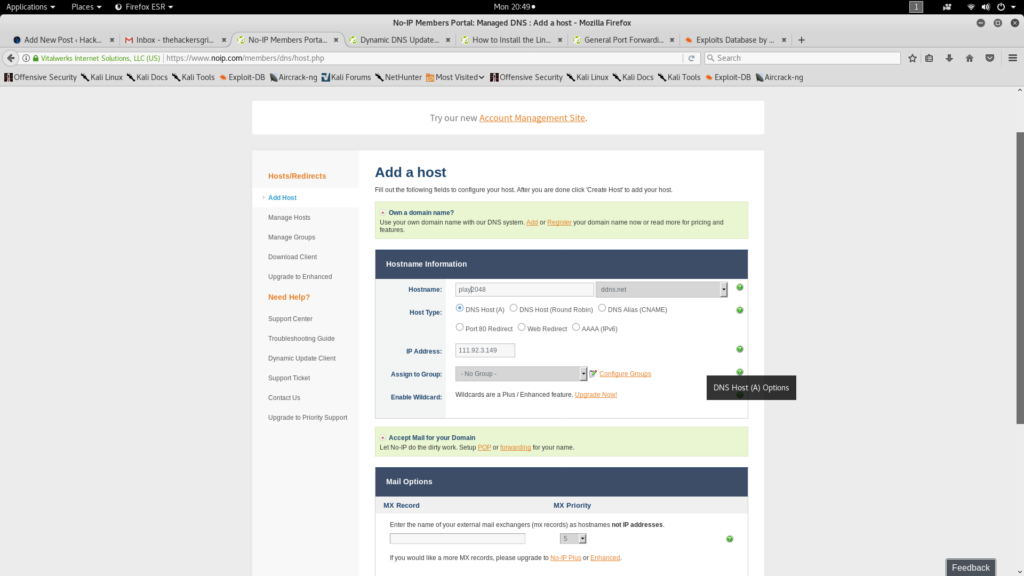
Setting up NOIP
Now setup Dynamic DNS by creating an account in NOIP and setting up Dynamic Update Client in that machine. If you haven’t done that, go ahead and click this link and follow this tutorial to setup one. It is an easy process and it wont take more than 5 Minute.
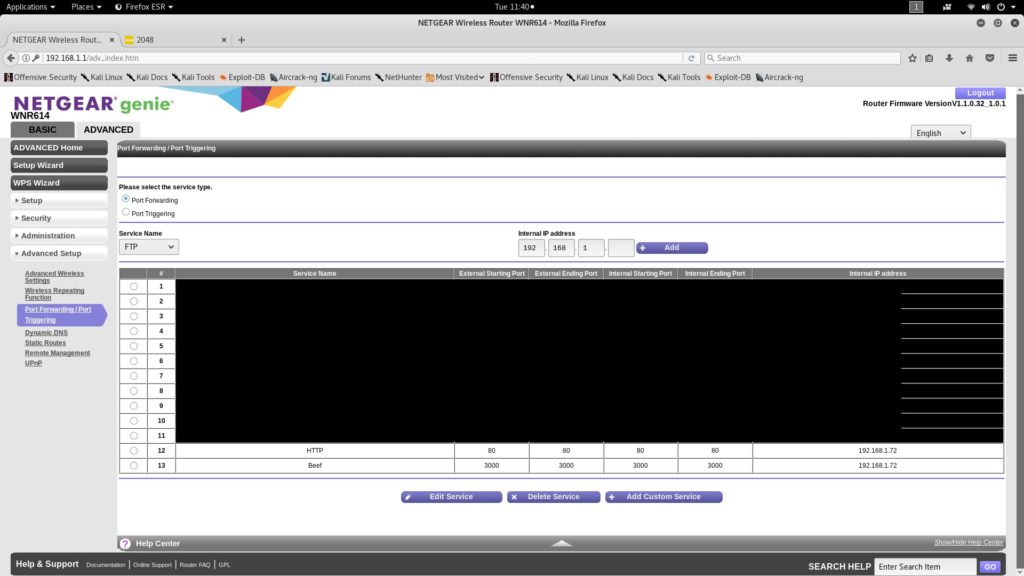
Port Forwarding
In order to forward packets from your router to the Raspberry Pi. You will have to add port forwarding rules to the router. In THIS case, we will have to forward 2 ports in order to make it fully functional (3, if you want SSH access to start or stop BeEF remotely).
Port 80 – It is the port that the server “listens to” or expects to receive from a Web client. We will be using this port to access 2048 game’s web page.
Port 3000 – It is the port that is used by BeEF. All the communication from and to BeEF will be going through port 3000. So in order to execute hook script and access the interface from a remote location, this port must be forwarded to the server.
If all the three steps are done correctly you will be now having a remote server which can be accessed from anywhere around the world.
The Attack
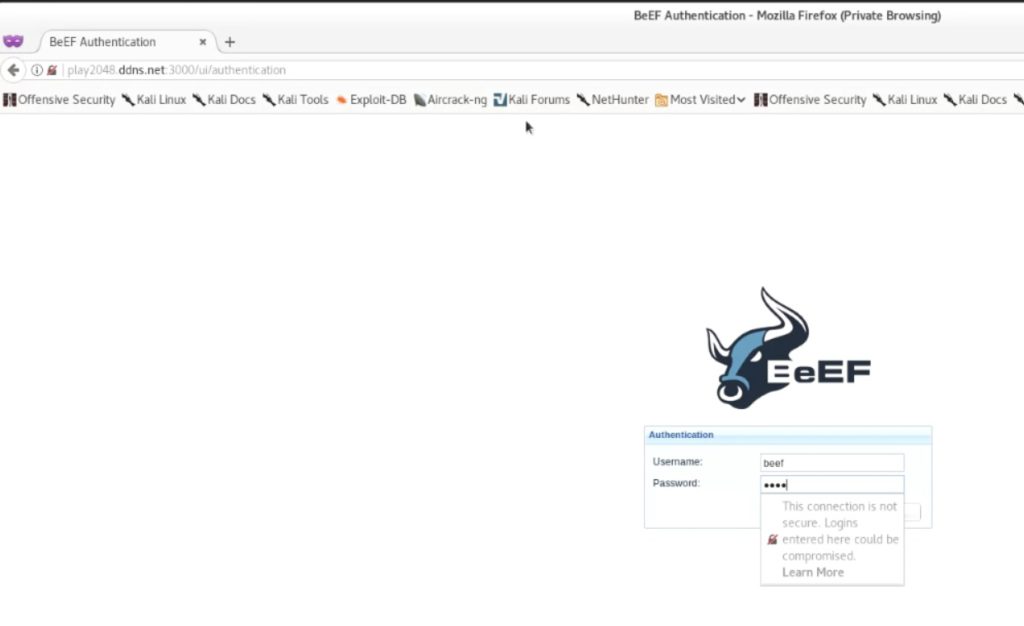
Now you can start beef and access the UI by issuing “http://play2048.ddns.net:3000/ui/panel”. If everything is done correctly, you will be seeing you BeEFs login page. Provide the credentials (beef:beef) and login to the dashboard.
All you have to do is send the link “http://play2048.ddns.net” to your victim. Since I am using a hostname instead of an IP address, people will think that it is a legitimate link.
When the victim click on this link, his browser will be hooked and can be viewed in the BeEF dashboard. You can use any attacking modules that are available in Framework remotely.



How to do Port forward without router.