ReelPhish – Defeating Two Factor Authentication Tutorial
ReelPhish – Defeating Two Factor Authentication using Real Time Phishing Attack Social Engineering Human Beings and their vulnerabilities have always been one of the loop holes in IT security. Even though the technology; software, networks and hardware,…
ReelPhish – Defeating Two Factor Authentication using Real Time Phishing Attack
Social Engineering
Human Beings and their vulnerabilities have always been one of the loop holes in IT security. Even though the technology; software, networks and hardware, have hardened, attackers are using common people, exploiting the lack of their knowledge to get what they want. Tricking people to do what they are not supposed to do – Social Engineering.
In the year 2017, we saw some of the most trickiest social engineering attacks in the history. Attackers used social engineering techniques leveraging fear of wannacry ransomware in peoples mind to send spam mails and perform phishing attacks to harvest user credentials. During another wave, hackers used Social Engineering to spread an Advanced version of RAT which could act as a Keylogger, capture screen and webcam, record voice, file browse, access command shell and all the common functions that can be performed by a RAT; named KHRAT across Cambodia. These are just a few.
Phishing
Phishing attack is a type of social engineering attack, where the attackers try to obtain user data such as login usernames and passwords, card numbers and other personal details by creating a fake login page that looks exactly the same as that of the real one.[AdSense-C]One way of executing this attack is the attackers drafts an E Mail or SMS, masquerading as a trusted entity, including convincing contents, a link to the fake page and send it to the victims. When the user opens the mail and click on the malicious link, he will be redirected to the fake page and enter sensitive information. Sometimes, this may lead to devastating results.
Two Factor Authentication
Using a login username and password has been the most widely used method for authentication and gaining entry to personal stuffs. But, as mentioned above, it is still vulnerable to Social Engineering Attacks. So it is always a good idea to add one more level of authentication, proving that it is really the right person who is requesting access to the data.
We could use “something we are”, such as a fingerprint or retina pattern, or “something we have”, like an access control card, a token or a USB Key. Two-factor authentication means using any of the two from below 3
- something we know
- something we are
- something we have
Two-factor authentication provides much stronger guarantees when compared to using just one of these means of authentication. In most websites, commonly used 2FA method is using a Login Username and Password and a One Time Password which is sent to our mobile phones or Email. These OTP expires in a short span of time and could not be reused again. In order defeat the two factor authentication, we have to do real time attacks.
ReelPhish
Fireye has come up with a new tool, named ReelPhish that enables us to do real time social engineering assessments. This tool works in 4 steps.
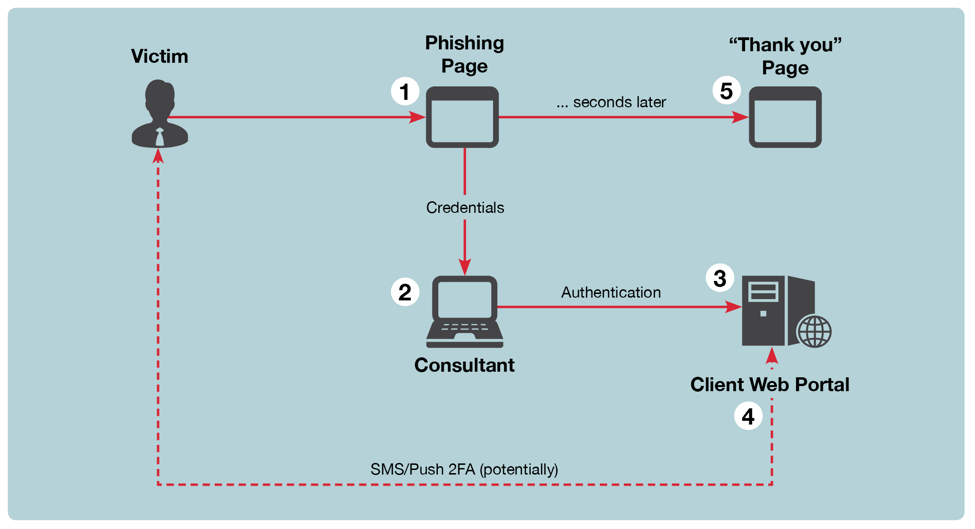
- ReelPhish generate phishing page that looks just like the original by copying the HTML, CSS and java scripts from the original site. It has two modules that works hand in hand
- The first module is a python script that runs on the attackers machine which will listen to a particular port for data that is sent by the phishing site generated by the attacker. It also runs a web browser which is installed on the attackers machine using Selenium Framework.
- The other module is embedded in the phishing site. This code will send the captured login credentials and other data to the first module which will be listening to this site.
- When the data is received by the first module, it will launch the browser using selenium and redirect the attacker to the legitimate website.
All the communication will be take place over a secure SSH channel.
Installation
The tool is available in the Github. You can download it by clicking the below button.[AdSense-A]Download
Now you will have to install selenium and other dependencies, for that, go inside the folder and run
pip install -r requirements.txt
Now the last thing to do is download and setup the Driver for your Browser.
Internet Explorer
- Download the Internet Explorer Driver Server for 32 bit Windows IE.
- Unzip the file and rename the binary to: IEDriver.exe
- In order for the Internet Explorer Driver to work, be sure protected mode is disabled. On IE11 (64 bit Windows), you must create registry key “HKEY_LOCAL_MACHINESOFTWAREWow6432NodeMicrosoftInternet ExplorerMainFeatureControlFEATURE_BFCACHE”. In this key, create a DWORD value named iexplore.exe and set the value to 0.
Firefox
- Download the latest release of the Firefox GeckoDriver for Windows 32 bit. Unzip the file and rename the binary to: FFDriver.exe.
- On Linux systems, download the Linux version of Firefox GeckoDriver and rename the binary to: FFDriver.bin . Linux support is experimental.
- Gecko Driver has special requirements. Copy FFDriver.exe to geckodriver.exe and place it into your PATH variable. Additionally, add firefox.exe to your PATH variable.
Chrome
- Download the latest release of the Google Chrome Driver for Windows 32 bit. Unzip the file and rename the binary to: ChromeDriver.exe.
- On Linux systems, download the Linux version of the Chrome Web Driver and rename the binary to: ChromeDriver.bin . Linux support is experimental.
[AdSense-B]