EITest Campaign Targeting Firefox and Chrome users
People are using HoeflerText notifications popup notification to make users install NetSupport Manager RAT and Locky ransomware. How does it work? The attack is pretty simple. Hackers send mails that contains malicious links that will redirect users…
People are using HoeflerText notifications popup notification to make users install NetSupport Manager RAT and Locky ransomware.
How does it work?
The attack is pretty simple. Hackers send mails that contains malicious links that will redirect users to malicious webpages. These mails were from botnets and they are coming from multiple IP addresses.
If the user is using google chrome or firefox, a pop up notification will appear with an update button stating they don’t have the HoeflerText font.
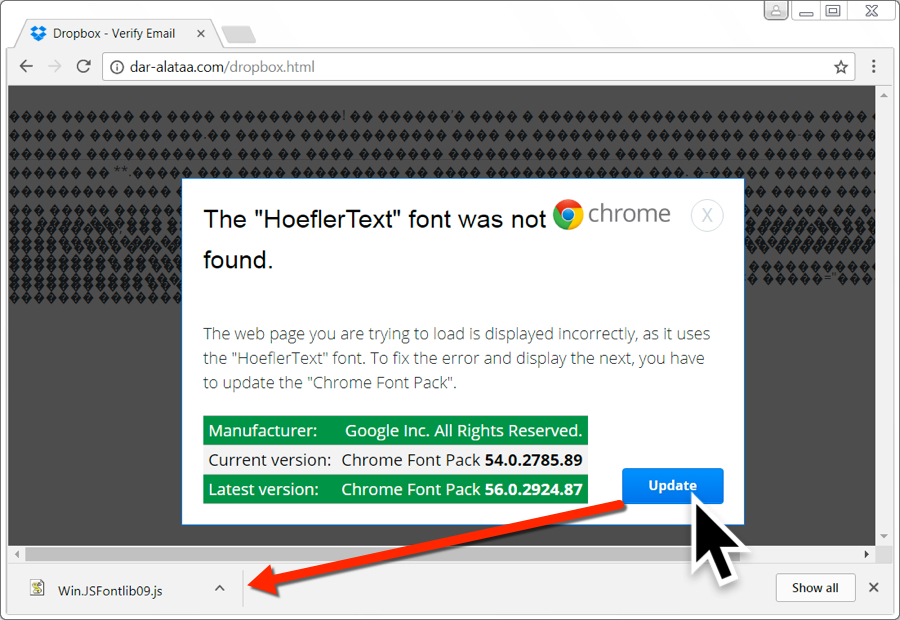

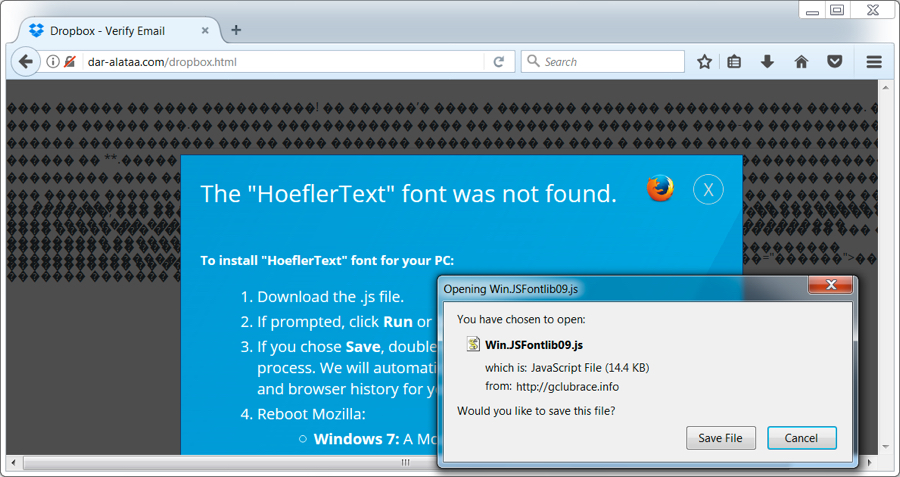
When the update button is pressed a malicious java script disguised as font library was returned .

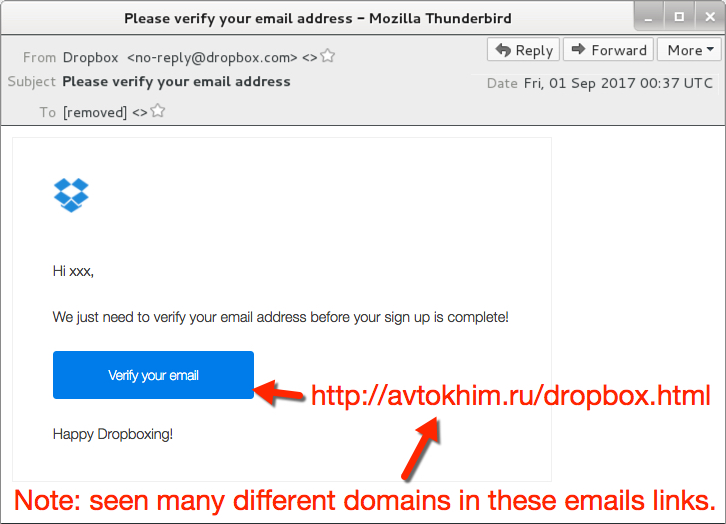
Ultimately, this infection wasn’t very innovative. The ransomware was the “Lukitus” variant of Locky, which has been out for a while, and it’s easily detectable. We’ve seen all the individual techniques used during the entire infection chain. However, it cobbled together some existing tricks like HoeflerText popups with fake Dropbox pages, so it briefly excited me as I looked into it.
Affected Browsers
Researchers have tried with various browsers. Till now, it looks like this notification is appearing only for Google Chrome, Mozilla Firefox, Opera and Vivaldi. When this same link is opened using Internet Explorer and Microsoft Edge this notification is not popping up. The same is for Tor and Yandex Browsers.
How not to be Victim?
This malware uses the old fashioned Social Engineering method of making the victim click on a malicious link in the Mail. So never click on any suspicious links or thumbnails from anyone in mail without verifying. Always keep your Firewall and anti Malware software updated.
Source:





Great, google took me stright here. thanks btw for this. Cheers!
Hi, google lead me here, keep up nice work.