Set up Metasploit Module for Apache Struts 2 REST ( CVE-2017-9805 POC )
A critical vulnerability that could completely compromise an apache struts web server was reported by a research team at LGTM (tracked as CVE-2017-9805 ( S2-052 )). Successful exploitation of this vulnerability could lead to RCE (Remote Code…
A critical vulnerability that could completely compromise an apache struts web server was reported by a research team at LGTM (tracked as CVE-2017-9805 ( S2-052 )). Successful exploitation of this vulnerability could lead to RCE (Remote Code Execution), taking full control over the server and a failed attempt can lead to Denial of Service.
Apache struts is an open source application for building web applications using java. All the web applications that are using this the famous REST application is now vulnerable to this attack. This plugin fails to handle XML payloads while de-serializing them.
Metasploit Module For Apache Struts 2 REST (CVE-2017-9805)
A metasploit module designed for exploiting this vulnerability was released today. Using this module, vulnerable websites can be exploited and easily gain a shell. The name of this module is ‘struts2_rest_xstream’
How to install Metasploit Module for Struts?
Watch Video Tutorial
Download Metasploit Module For Apache Struts 2 REST (CVE-2017-9805)
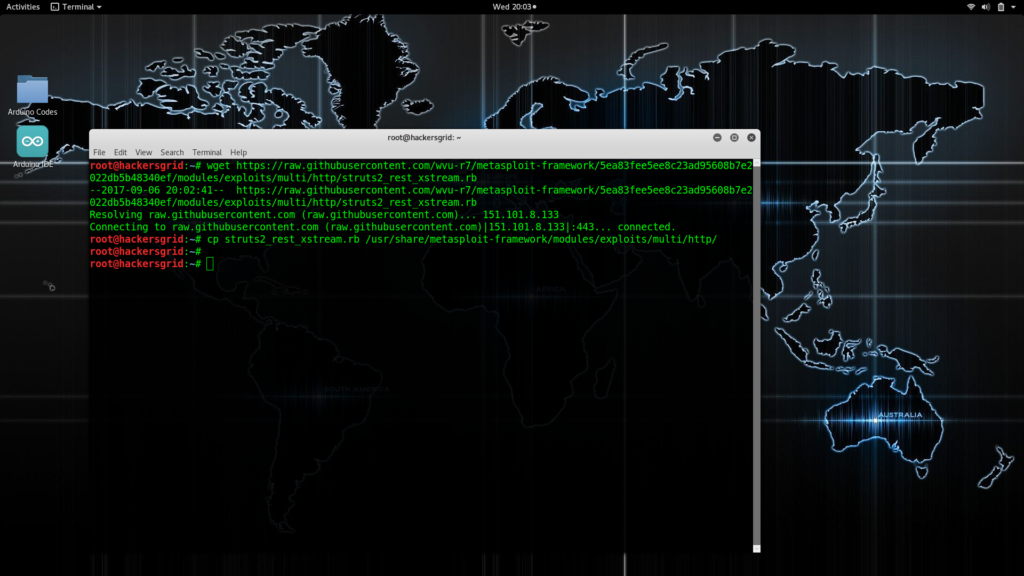
First you have to download the module by executing the command
Next you will have to move this downloaded file to metasploits directory
cp struts2_rest_xstream.rb /usr/share/metasploit-framework/modules/exploits/multi/http/
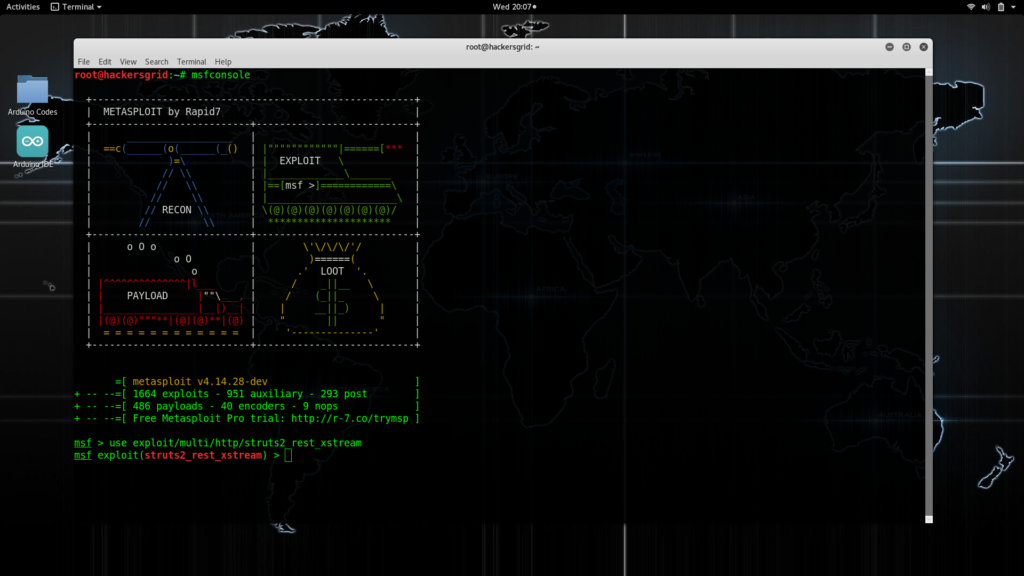
Now start metasploit to check whether the module is being loaded correctly.
msfconsole
Now load the module by running
use exploit/multi/http/struts2_rest_xstream
We can see that the module is loaded correctly. Now type
show options
To view all parameters to set to execute the attack. If you face any difficulty during the installation, please let me know it in the comments.
Update 8/9/2017
This is the updated version of Metasploit Module For Apache Struts 2 REST (CVE-2017-9805)
https://github.com/rapid7/metasploit-framework/pull/8924/
Vulnerable Versions
Apache Struts 2.5 through 2.5.12 that are using REST are vulnerable to this attack.
Happy Hacking…



The MSF module link is out of date, use the latest commit in this PR:
https://github.com/rapid7/metasploit-framework/pull/8924/
thanx for the info Smrtz..
This will be updated in the post. 🙂
bro , pls share remaing steps to run