BeEF 101 – Browser Exploitation Framework
In this post, I will explain BeEF, how to install it and test the installation by performing a small attack on my system.
BeEf or Browser Exploitation Framework is one of the most powerful arsenals of Kali Linux, which enables client side attack against web browsers. JavaScript can be very powerful and dangerous. This framework can takes advantage of XSS or Cross Site Scripting which is a critical Vulnerability (as mentioned by OWASP) found in webpages, to inject java script and take control over the browser and sometimes even the whole system.
Video Tutorial
How to Install BeEF?
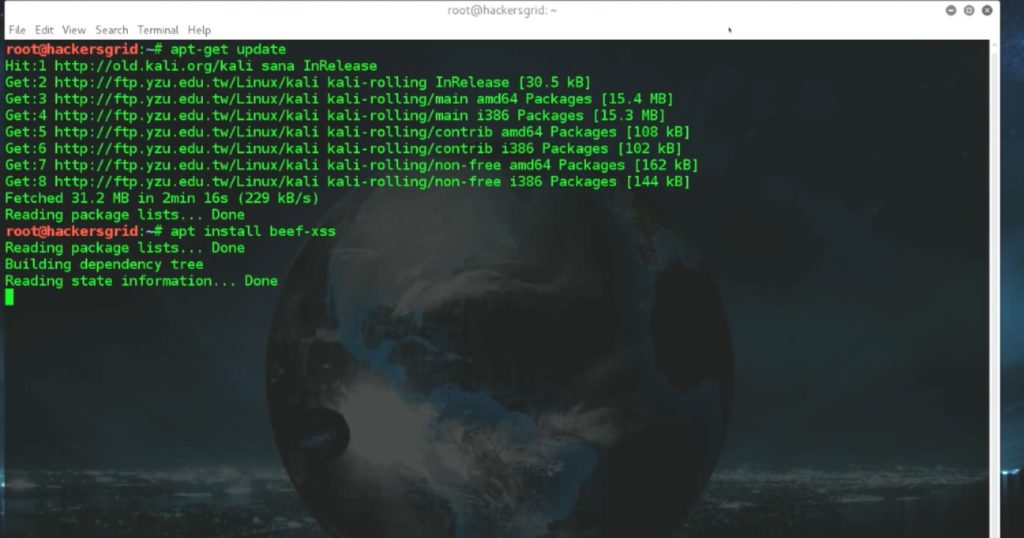
Installation of BeEF is pretty simple. All you need is a Kali Linux machine that have an active internet connection. First make sure that you have the right repositories added in /etc/apt/sources file. Once added, we can install this framework by executing two commands. Fire up the terminal and execute
#apt update
#apt install beef-xss
Launching BeEF
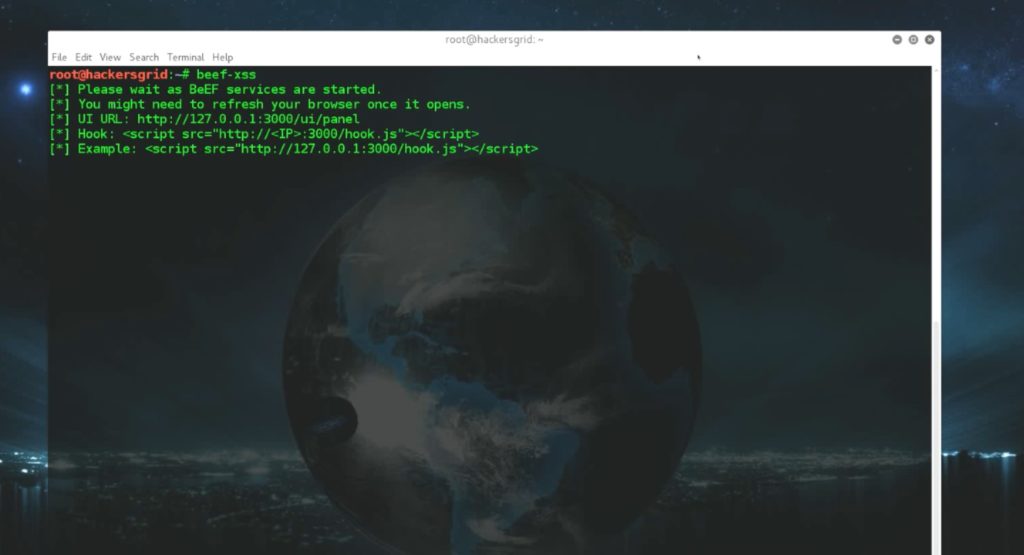
Once it is installed, you can start beef by simply typing
beef-xss in the terminal
Here we get to see somethings which we will be using it in the future. You will be seeing the word hook.js multiple times when you start the framework. Before going further, you should know what is ‘BeEF hook’, which is the seed of the attack.
What is BeEF hook?
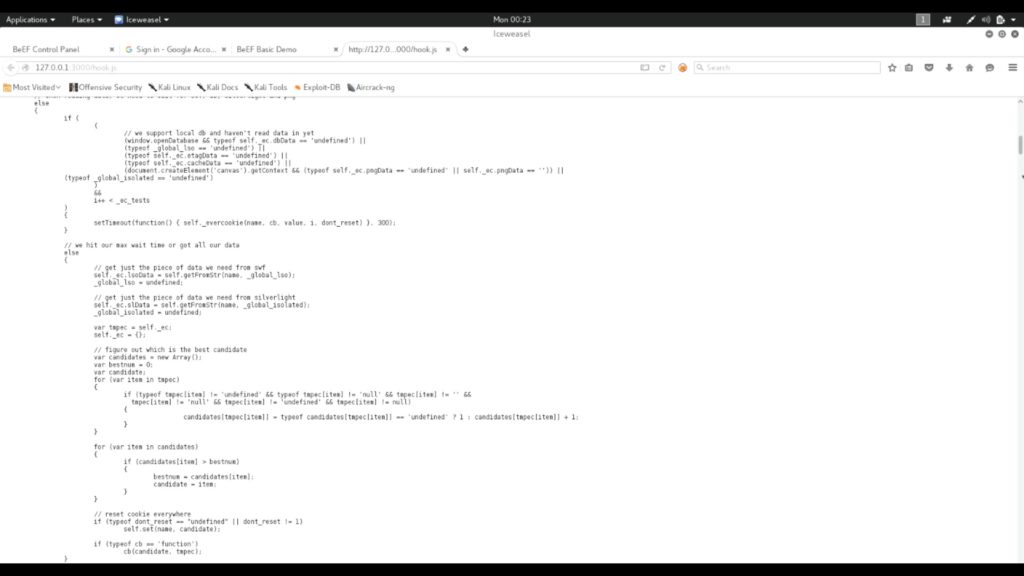
BeEF hook is a carefully crafted java script which is stored in the attackers machine (server) which must execute in the target web browser in order to successfully compromise the it. When this code is executed in the target machine, it will send back so much valuable information about the victims machine and browser. It also allows other modules in BeEF to run against the victims machine.
This is how hook.js looks like.
Accessing the Interface
Most of the time, it will automatically start browser for you but if it didnt, you just have to open the browser and go to
http://:3000/ui/panel
Or if you are using the same machine, you can access it using
http://localhost:3000/ui/panel or http://127.0.0.1:3000/ui/panel
Default Username : beef and Default Password : beef
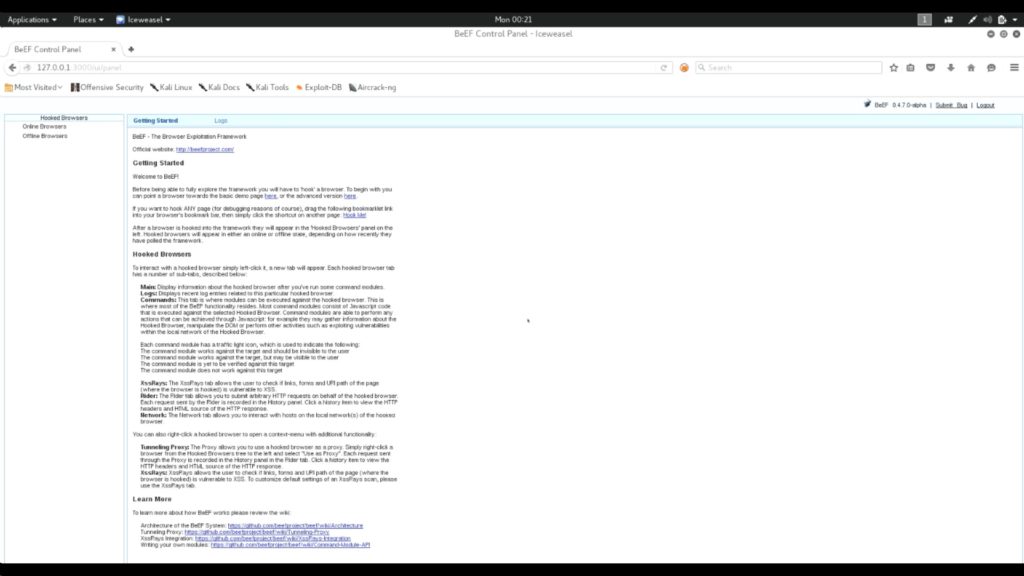
After successful submission of credentials, you will be redirected to the dashboard.
This is the main control panel. Here you can see all the details about all hooked browsers, its IP address, version, availability, possible attacks etc. From here you can launch attack against various targets that are up and online.
Testing – Our First Attack
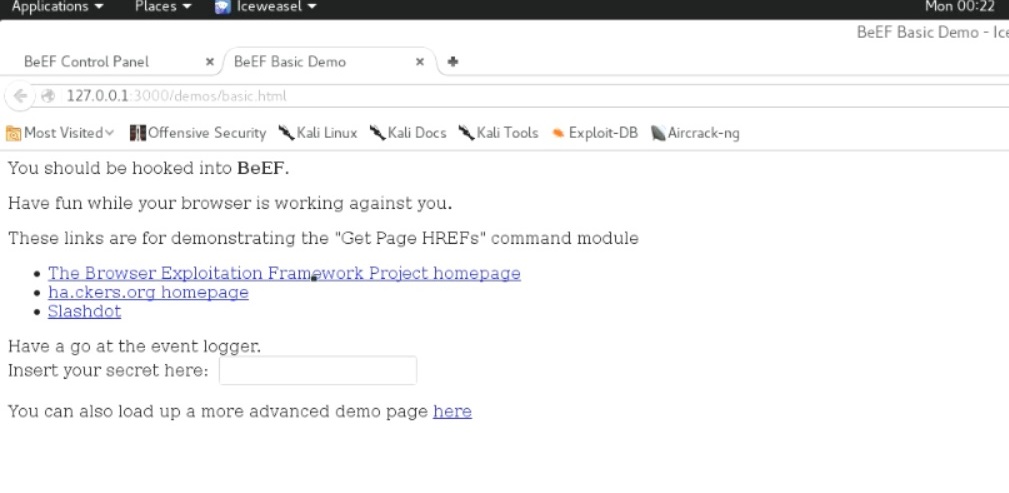
Everything has worked perfectly so for, now its time to check how it performs. For that I will be opening a demo web page in which the hook.js is already embedded and see if it is hooking my browser and launch a small phishing attack.
I have opened a demo page and as you see in this image, it had already hooked my browser.
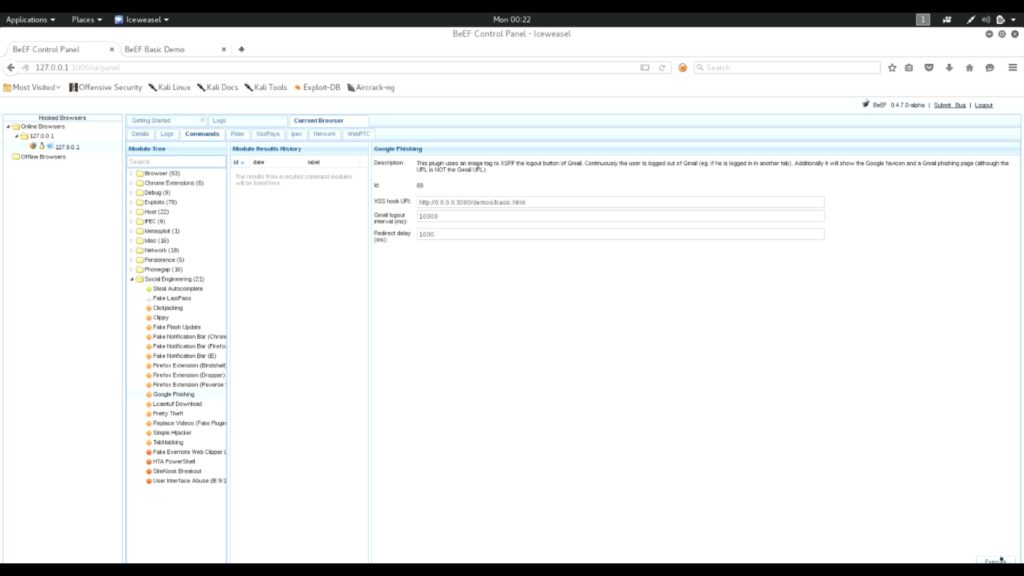
From the command tab, I am going to select Google Phishing module from Social Engineering category. Once it is selected, click on execute.
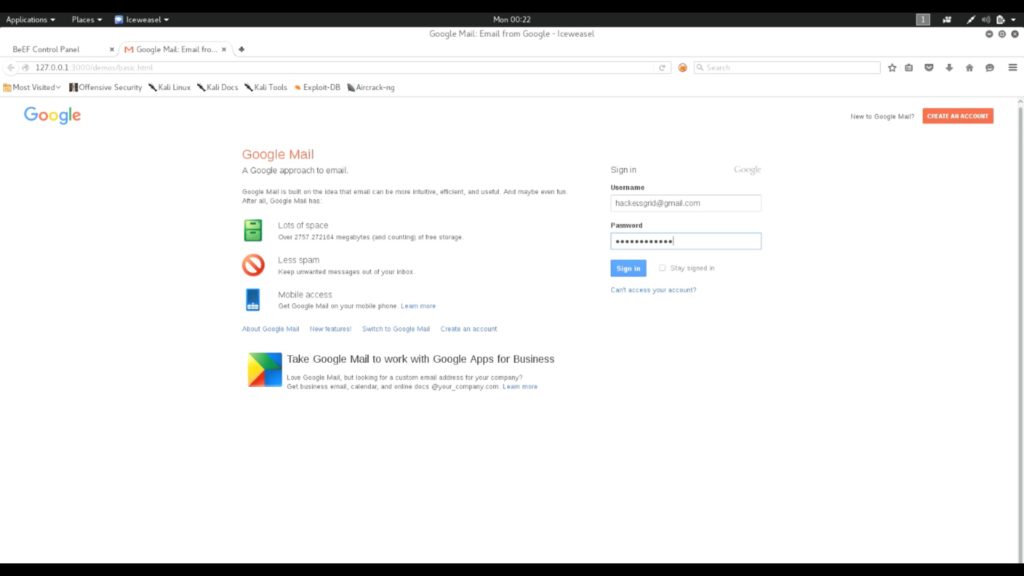
As you can see the demo page has changed to a fake google login page.
When the user tries to login from the browser, the credentials will be send back to the server and the user will be redirected to the real login page of gmail.
This is just a glimpse of what you can do with this framework. As mentioned earlier, this is a framework with endless possibilities. Everything is limited by your imagination.







The article is well explained. Thanks. Consider zooming and cropping the image before uploading. Images are not clear.