Malware author offers Cobian RAT for Free hiding an Ugly Truth
Researchers at Zscaler ThreatLabZ has observed a malware writer, offering a new class of malware, dubbed cobian RAT for free in the darknet but.
What is DarkNet?
The Dark Web then is classified as a small portion of the Deep Web that has been intentionally hidden and is inaccessible through standard web browsers.
Dark-Net is a cluster of computers meshed together in order to form a network. It is a place where your identity or IP is very very very difficult to track. In order to access a computer in the Dark-Net, you will need special softwares installed on your system.
Click Here to Know More About Darknet
About Cobian RAT
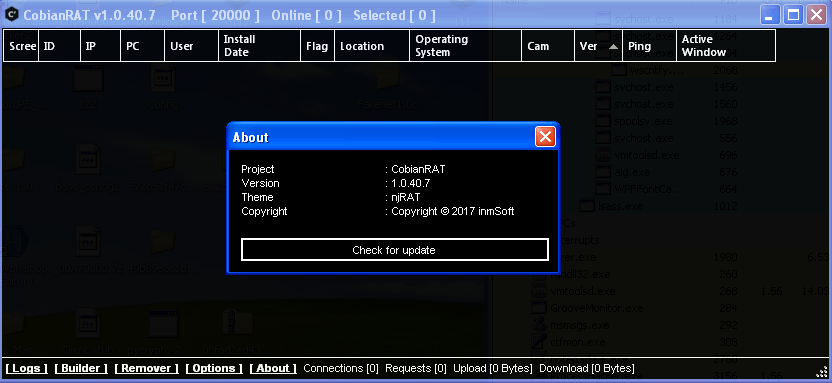
Cobian RAT is new class of malware which is based on an old RAT known as njRAT whose code was obfuscated by a variety of .NET tools that made it difficult for antivirus and malware scanners to detect the RAT.
Usually, news about these kinds of exploits are published in darknet websites where the authors provide their contact information. Users who are interested could contact the author, negotiate the price and buy these exploits. It was similar in the case of Cobian RAT. The news about cobain RAT Builder kit, which allowed hackers to create Cobian RAT payload, was published in so many darknet forums. But what caught attention was, the author was customizing it according to users need and was offering it for free.
“This RAT builder caught our attention as it was being offered for free and had lot of similarities to the njRAT/H-Worm family, which we analyzed in this report.”
The Ugly Truth
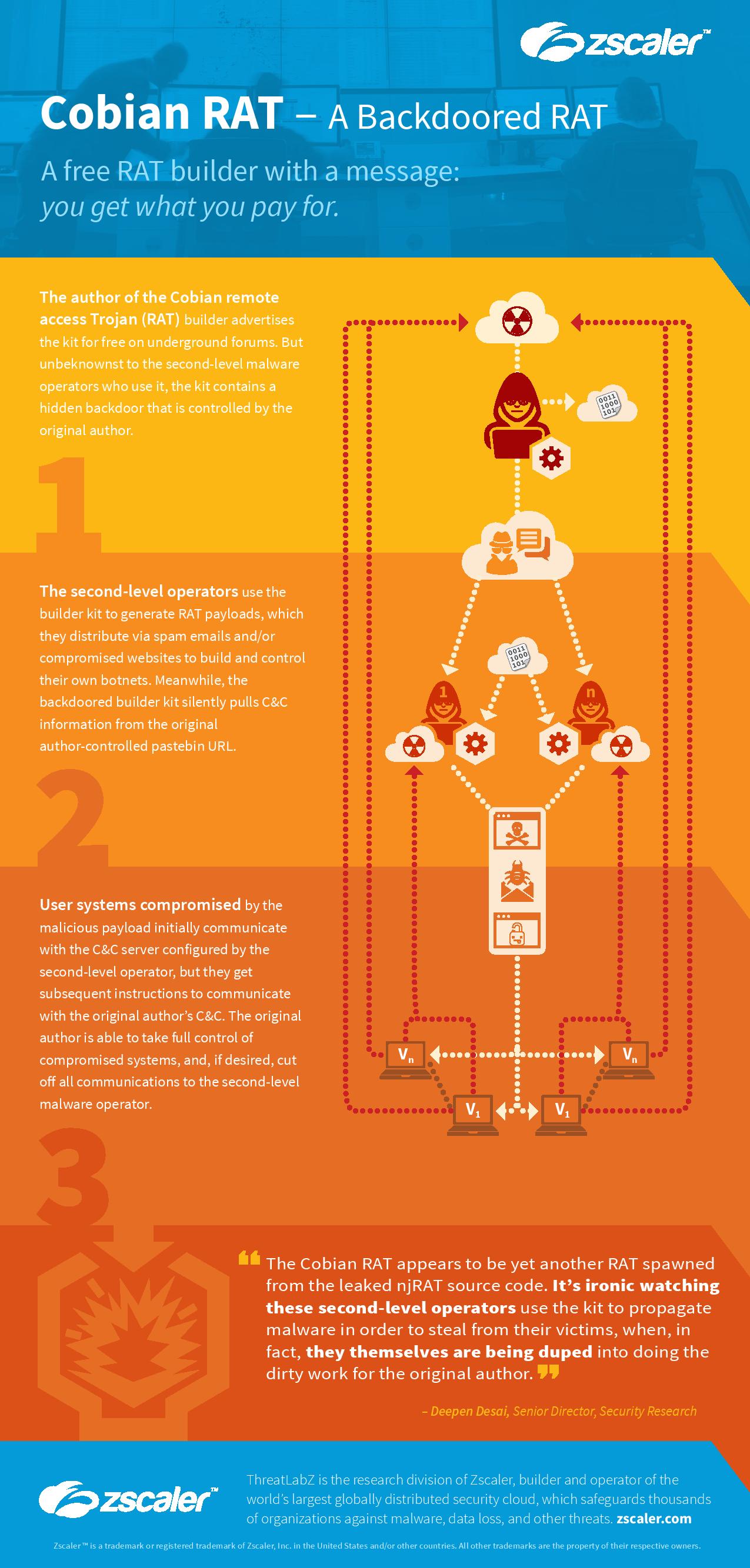
After a detailed research, it was observed, Cobian RAT was not just a RAT. It was a malware with a backdoor that allowed the author of the malware to control the systems infected by the malware payloads that were generated using this builder kit.
This allowed the real author to take control of all the machines that was infected across all the Cobian RAT botnets in which the operators used the builder kit and yes thats a huge number.
The author can even change the CnC server address of the victims configured by the secondary level operators.
It is ironic to see that the second level operators, who are using this kit to spread malware and steal from the end user, are getting duped themselves by the original author. The original author is essentially using a crowdsourced model for building a mega Botnet that leverages the second level operators Botnet.
This RAT can act as a Keylogger, capture screen and webcam, record voice, file browse, access command shell and all the common functions that can be performed by a RAT.







Hello, thank you for writting this!
Great Website. Really enjoyed reading.
Kiduveee