“adoḅe.com” or “adobe.com” – Active Homograph Attack Seen in Wild
“adoḅe.com” , “adobe.com” notice any difference?
Hackers have been performing homograph attack using punycode encoding methods on look alike domain name – ‘adoḅe.com’ ( similar to adobe.com ) to spread Malware for a while.
What is HomoGraph attack?
Homograph attack is an attack that takes advantage of non ASCCI characters that looks similar but different in different languages. In this type of attack, the attackers buy domain names that are similar to the existing ones and use this name for phishing and other attacks. Since the domain name is similar, people wont be suspicious.
eg – http://www.g00gle.co.uk and http://bl00mberg.com
For DNS to handle non latin addresses, they are encoded in a special format known as Punycode and all browsers translate non-ASCII URLs into Punycode in the background before performing a DNS lookup. A this type of domain name always starts with an xn-- and then contains ASCII characters of the original address followed by encoded Unicode data.
How does it work?
Using the above mentioned method, in most of the browsers, xn--adoe-x34a.com is seen as “http://adoḅe.com/” making the users think that they are visiting legitimate website “http://adobe.com/”
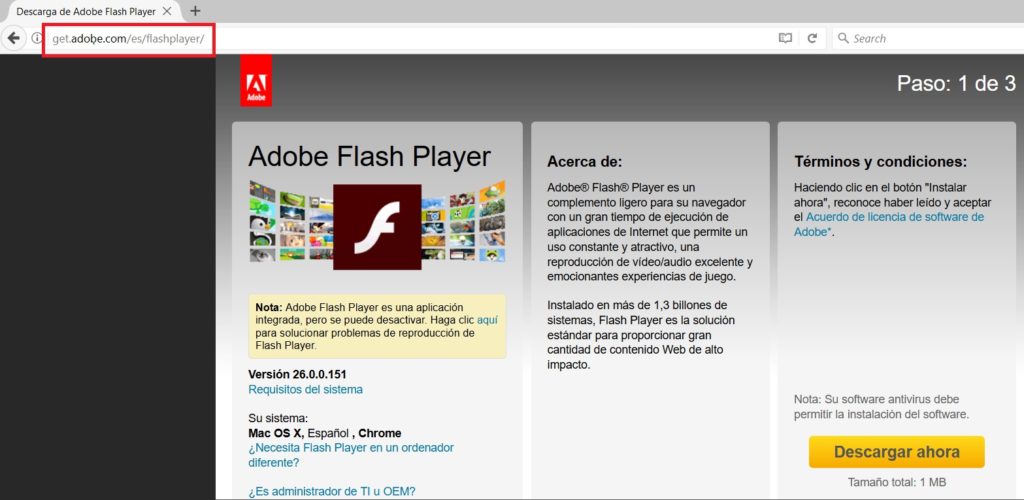
“This site was hosting malware on http://get.xn--adoe-x34a.com/es/flashplayer/flashplayer26_pp_xa_install.exe
This will be seen as http://get.adoḅe.com/es/flashplayer/flashplayer26_pp_xa_install.exe in browsers, confusing the victim.” A security researcher Ankit Anubhav, reported this active attack in pastebin a few hours ago.- Click here to see original post
The site resembles adobe’s flash player download page and looks legitimate. Once the victim enters the site, it will prompt the user to download a file named “flashplayer27_pp_xa_install.exe” which is actually a malware. When this script is downloaded and installed malicious script will start to run in the victims machine.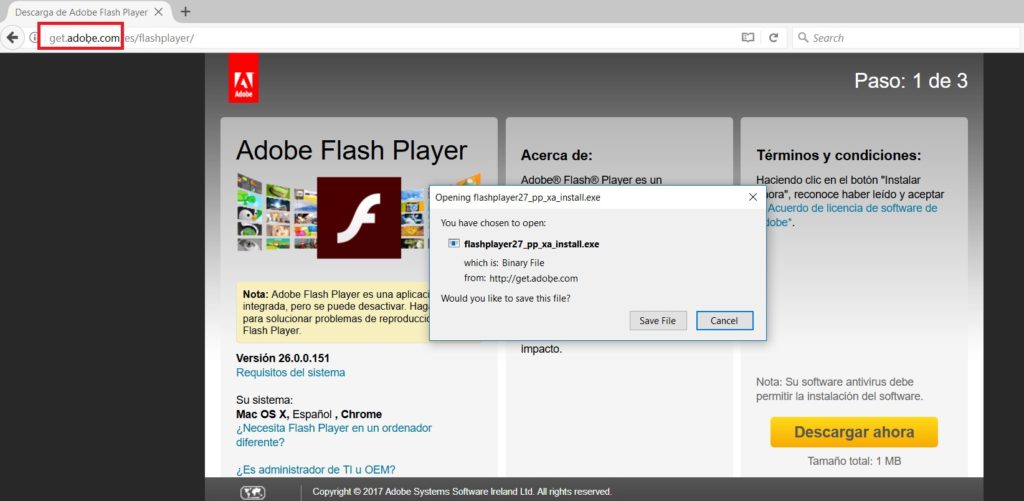
The actual link to the file is “http://get.xn--adoe-x34a.com/es/flashplayer/flashplayer27_pp_xa_install.exe” but in a browser, it will be seen as “http://get.adoḅe.com/es/flashplayer/flashplayer26_pp_xa_install.exe”, misleading the users with fake URL.
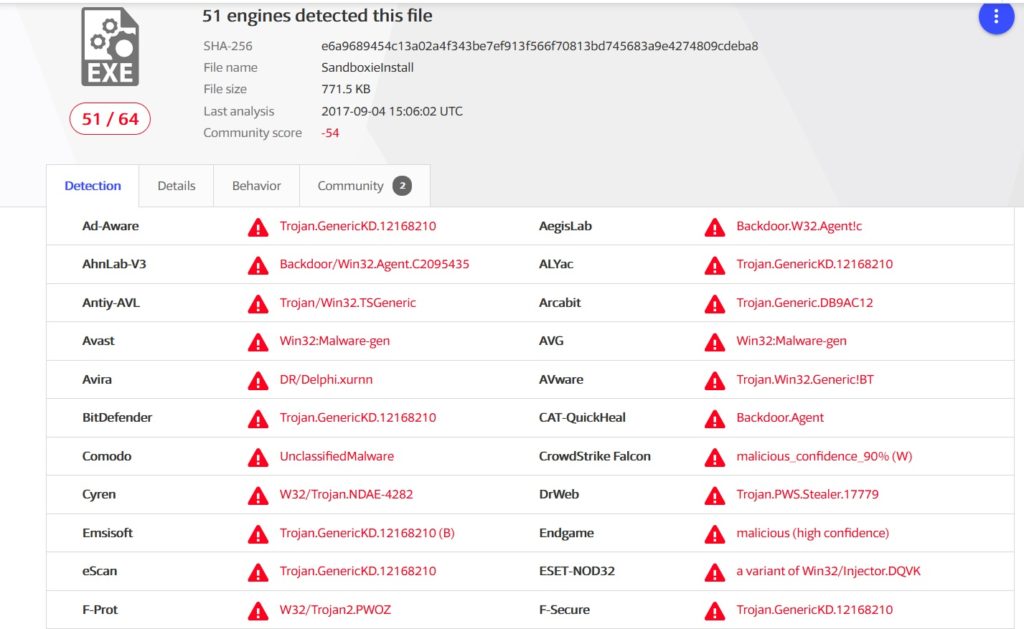
Antivirus Detection
When this file was uploaded to Virus Total, 51 out of 64 engines detected this file as malware.
So it is always a good idea to have a good antivirus/antimalware software updated.
File Analysis
SHA-1 – fbf926d1b1f7670169b9c71b282f2327f041361c
Authentihash – a9a9bc6bcf9c5ede498fb5285064c18ea45e3bdd57667449274b63759f7a3459
Imphash – 70c93e85e53618945476598c6cd1e7d7
File Type – Win32 EXE
Magic – PE32 executable for MS Windows (GUI) Intel 80386 32-bit
SSDeep – 12288:PGH4CFVQzKL+Q2e74ienjqg1ywp6ukDHx1vGdA/6AvB0HNx8hMfHTqLAHw2idHYg:OYCZL+Q2Ipwpdqu+jMfzq0HmdH4gP
TRiD – Win32 Executable Delphi generic (37.4%) Windows screen saver (34.5%) Win32 Executable (generic) (11.9%) Win16/32 Executable Delphi generic (5.4%) Generic Win/DOS Executable (5.2%)
File Size – 771.5 KB
Source: https://pastebin.com/52WEZADt