Ubertooth One Getting Started – Kali Linux
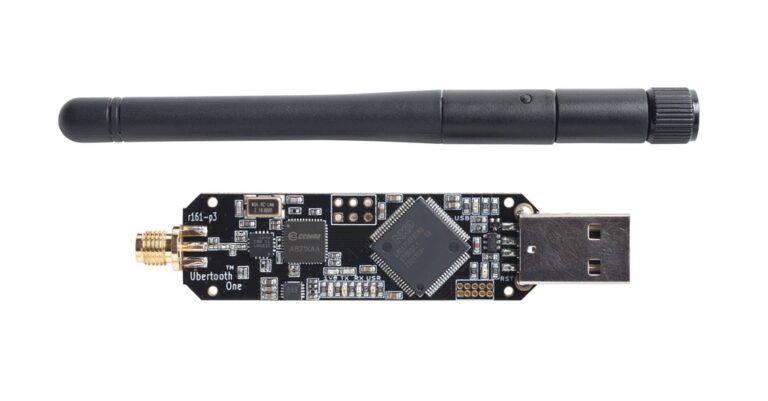
Ubertooth One The Ubertooth One is one of the best and cheap hardware tool you can put your hands online for Bluetooth Low Energy device penetration testing. It is basically an open source development board that works in 2.4 GHz Frequency which is widely used for wireless communication protocols such as WiFi, Zigbee etc. Of…