Hackers Finding Creative Ways for Exploiting Log4J Vulnerability
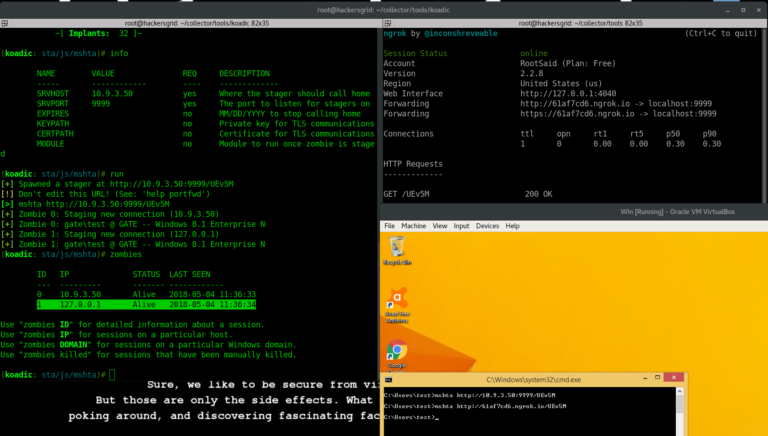
A new vulnerability has been found in the widely-used Apache Log4j Java-based logging library that leaves millions of websites vulnerable to attack. This is a big problem because it can be exploited with a single string of text. Hackers are exploiting Log4j vulnerability to target Windows machines with different ransomware as well as remote access Trojans. The attack leverages the remote code execution (RCE) flaw to download different malicious files from a remote server that will compromise the server.
What is Log4J vulnerability?
Logging is a very important part of any Java application, and Apache Logging Service Log4j has been around for a long time. Log4j is a logging library that may be used for both logging and front-ending other logging applications. However, a new vulnerability has been found in the popular Apache Log Library – Log4j. The main problem with this vulnerability is that it can be exploited with a single string of text.
Exploiting Log4J Vulnerability
The Log Library vulnerability is a remote code execution (RCE) flaw that can be exploited by sending a specially crafted message that will be logged, to the target server. The malicious payload is hidden in any of the header fields that will be logged, and when parsed it will execute the code on the target machine. This can allow hackers to download different malicious files from a remote server that will compromise the target.

By default, JNDI lookups are enabled, and the log4j 2 components may execute these JNDI instructions. For example, an attacker may include a JNDI command in a request to download and execute a harmful file as part of the header if log4j 2 is logging all requests.
If a harmful JNDI command is found, it will be processed and the malicious file will be downloaded to the server. So all an attacker has to do now is find some logged data and then insert something like this.
Read More About this in the Previous Article – Log4J Vulnerability, Exploits and Mitigation Explained
How are Hackers Exploiting Log4j Vulnerability?
The main problem with this vulnerability is that it leaves millions of websites vulnerable. This means hackers have a good chance of exploiting these servers, and then infecting other machines on the network if not patched in time.
In the wild, hackers are exploiting this vulnerability with a single string of text. Hackers can execute commands on web servers using RCE flaw to download different malicious files from a remote server that will compromise the target. In most cases, they use ransomware or other malware to attack Windows machines and have been seen exploiting Log Library vulnerability in order to install backdoors on systems.
The Khonsari ransomware is a new threat that spreads via the Apache Log4j Library vulnerability exploiting Windows machines. Once it infects a system, it will encrypt all files on the drive and demand ransom in order to decrypt them again.
Ransomware is just one-way hackers are exploiting this flaw. With RCE flaws being used for installing backdoors to gain further access to the server. A backdoor is basically an entry point that gives the hacker access to the target system. They can use this backdoor to install other malware on the machine or take full control of the system.
There are reports that the hackers are exploiting this vulnerability to create a botnet. A botnet is a collection of compromised systems that can be controlled by the hacker for different purposes, such as launching DDoS attacks or sending spam.
Crypto-currency mining is a way for hackers to use the resources of compromised computers in order to mine crypto coins and then monetize them.
They are also used for other harmful purposes such as exploiting their servers in order to send spam emails and infect thousands of machines, due to their widespread nature.
Log4j Vulnerability Mitigation?
Due to the widespread nature of this vulnerability, it is essential that servers are patched immediately in order to avoid any attacks exploiting Log4j Library.
The Log4j logging utility has been fixed and the patch is made available to the public by the Apache Software Foundation (ASF) to help prevent this problem.
In previous versions, you could prevent an attack by setting the system property log4j2.formatMsgNoLookups to true by adding the following Java parameter: -Dlog4j2.formatMsgNoLookups=true
You can also prevent this vulnerability by removing the JndiLookup class from your classpath.
To defend against this attack, many WAF rules have been implemented by CDN and Firewall providers like Cloudflare.