KHRAT Trojan Updated Version Spreading across Cambodia
Researchers at Paloalto networks has discovered an updated version of previously known RAT named KHRAT is spreading across Cambodia with new.
About KHRAT
The first appearance of this trojan was a few months back. It was a dropper that the hackers used to disguised as an Adobe Reader installer and installs yet another new custom remote access tool (RAT). This RAT was named KHRAT based on the Command and Control Server used (kh.inter-ctrip.com) which was in Cambodia.
This RAT can act as a Keylogger, capture screen and webcam, record voice, file browse, access command shell and all the common functions that can be performed by a RAT.
How Does it works?
A few days back, people at Cambodia started receiving spam mails containing malicious attachments related to Mekong Integrated Water Resources Management Project (MIWRMP). These mails contained an atachment named “Mission Announcement Letter for MIWRMP phase three implementation support mission, June 26-30, 2017(update).doc”.
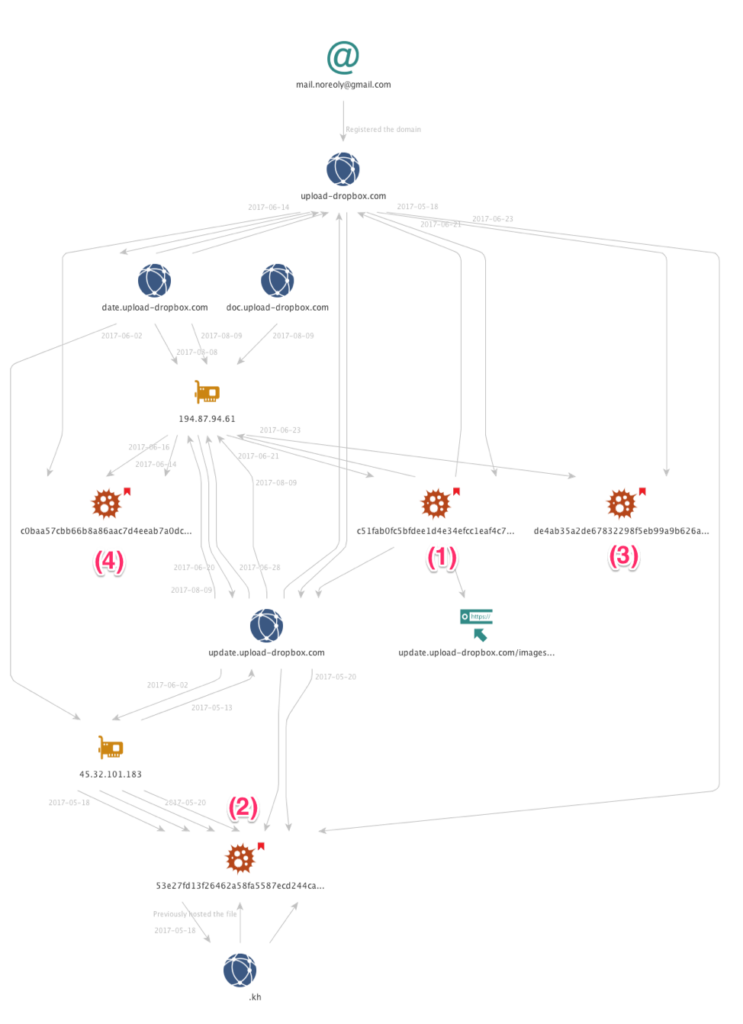
This attachment connects to a Russian IP address (194.87.94.61) that uses the “domain update.upload-dropbox.com” which will make the victims think that it is connecting to a legitimate dropbox server.
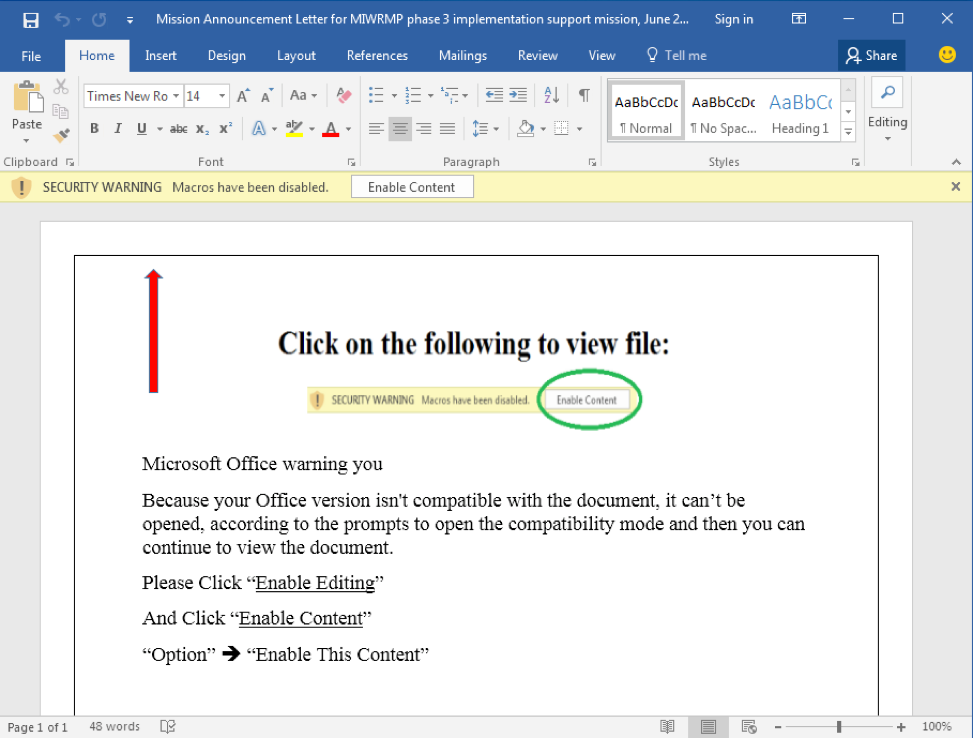
Once the file is downloaded and opened, hackers used social engineering skills to make the users enable macro content, which will run the VBA code which in turns executes the trojan.
When the macro content is enabled, the content of the document changes to “Because your Office version isn’t compatible with the document, it can’t be opened, according to the prompts to open the compatibility mode and then you can continue to view the document.” which will make the users think that it is actually a compatible issue, which is still another distraction.
Once this trojan start running, it will make its subprograms looking like legitimate task regsvr32.exe, which then starts some decent looking applications and starts calling java functions.
Protecting Yourself from KHRAT
- Never open files or links in suspicious mails or download attachments without verifying.
- Patch your system regularly with latest updates.
- Use a good Antivirus Software – Anti Malware Sytem
Source: PaloAlto Networks




bing took me here. Cheers!