OWASP Top 10 2017 Security Threats Explained – PDF Download
What is OWASP?
OWASP or Open Web Application Security Project is an unbiased open source community focusing on improving the security of web applications and software. OWASP, formed as wide group of like minded people has now grown and provide free information about the flaws and application security to developers, corporations and universities world wide. All the documents and information contained with in are open and free and anyone from anywhere around the world can contribute to OWASP. Every year OWASP updates cyber security threats and categorizes them according to the severity.
Top 10 Web Application Security Threats of 2017
OWASP has now released the Top 10 Web Application Security Threats of 2017.

Download PDF
The complete pdf document is now available for download. Download it by clicking the link below[AdSense-A]Download
Threats Explained
A1 2017 – Injection Attacks
All the input fields or the data source can be an injection vector. These types of attacks occur when the attacker can send maliciously crafted data through an input field to a web application. If there is a no proper validation of the input methods, attacker can cause the web application to malfunction and cause data loss, corruption, denial of service or even pawn the entire host.
These types of attacks are found in SQL, LDAP, SMTP headers, XML, ORM queries etc and are easy to discover an exploit using automated scanners and fuzzing software.
A2 2017 – Broken Authentication
Attackers will have access to thousands of username and password combinations which can be used for easily brute forcing a username password combination in a web application lacking bruteforce prevention methods. Moreover, if the session tokens and cookies are not expired after a particular time, valid sessions can be created by an attacker and gain access to confidential data.
Consider the case of a public computer. A person uses this computer to access a website. Instead of login out, the user simply closes the web browser and walks away. If proper session timeout is not employed in the web application, another person using the same computer can access the previous sessions becuase the previous user is still authenticated.
A3 2017 – Sensitive Data Exposure
Man in the Middle attack is a common attack that is employed by the attackers to steal data. A person in a network can simply sniff all the data packets that is flowing through that network. If the packets in transit are not encrypted, it is very easy to collect the sensitive data passing over the network.
Data should be always encrypted; in storage as well as in transit. When cryptography is employed we should make sure that there is strong key generation and management, strong algorithm, good password hashing techniques and proper protocol and cypher usage.
A4 2017 – XML External Entities (XXE)
Attackers can easily exploit vulnerabilities in XML processors, by uploading malicious XML files that may contain unwanted codes and thus exploiting the vulnerable code, dependencies and integration processes.
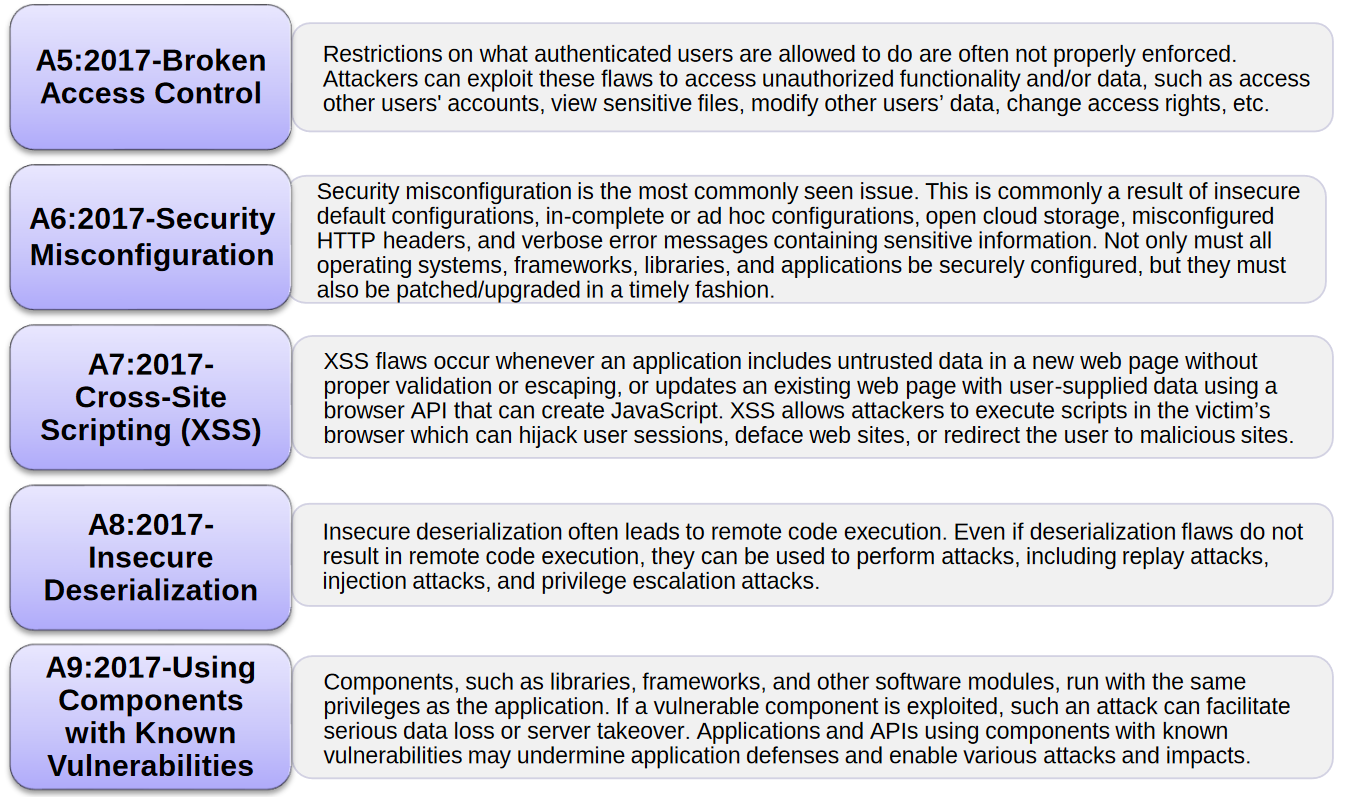
A5 2017 – Broken Access Control
This is another common way of approaching sensitive information by an attacker. Here, the attacker can bypass access control regulations by simply altering the contents of the URL or simply using intercepting tools such as ZAP or Burp Suit to intercept and alter the request.
Using this method, if web application is not properly configured, attacker can escalate the previlages; acting as a logged in user when he is not actually logged in, or act as an admin when he is logged in as a normal user.
A6 2017 – Security Misconfiguration
Using spiders, automated scanners and fuzzers like Nikto, attackers can easily identify pages that are unused, version and vulnerabilities in that version, files and folders, logs that are publicly available to gain information about the whole systems and gain access to it.
These flaws can give attackers unauthorized access to confidential data and /or functionalities which will lead to sensitive data exposure and sometimes even complete system compromise.
A7 2017 – Cross Site Scripting (XSS)
Cross Site scripting occurs when Web Applications accept user inputs with out properly validating and sanitizing the inputs. Attackers can enter executable codes in the input fields which will run when it is viewed in a web page when the code is parsed. This is similar to the injection attacks as the browser cannot find the difference between the code to be executed and code to be displayed.[AdSense-A]Cross Site scripting when combined with other weakness can cause massive impact on the attack. Attackers can gain access to cookies of valid users, which can then be used to create a session. Tools like BEEF (Browser Exploit Framework) can take advantage of the Cross Site Scripting Vulnerability and perform highly sophisticated attacks on valid users.
A8 2017 – Insecure Deserialization
There are tools that can point out deserialization flaws, but in order to confirm it, human assistance is required. If this vulnerability is exploited, attackers can run remote codes in the vulnerable server.The best preventive action is to reject the serialized objects from untrusted sources or use mediums that will permit primitive data types only.
A9 2017 – Using Components with Known Vulnerabilities
Absence of periodic updates and upgrades and application of patches on outdated system software, OS and firmware can cause a great impact on the cyber security. Older versions of software may be having various vulnerabilities that might have been patched in the newer versions. Once a vulnerability is disclosed, exploits are made publicly available. These exploits can then be used to successfully compromise the vulnerable version. [AdSense-C]If you fail to keep your system software updated or regularly scan for vulnerabilities, you could be in trouble.
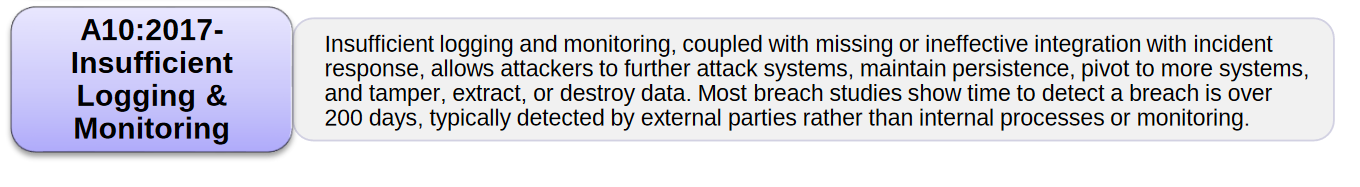
A10 2017 – Insufficient Logging and Monitoring
Lack of proper logging and monitoring various events happening inside and outside the web application is something that attackers rely on. Events such as login attempts and failed login attempts, IP address of incoming connections, important events such as a high value transactions must be logged and monitored regularly. By doing so, we can understand what all things are going on and will be useful for forensic investigation.