The Unfortunate Reason Why Phishing Keeps Happening | Phishing Explained
Each year, millions of people are tricked by phishing attacks. See why they happen and how to protect your company from them in this article!
“Hey, I think one of your employees emailed me and said they wanted to show me something about our account.” Said the stranger on the other line.
“That’s not possible.” Replied my boss from across the room. “We don’t have any information like that up for grabs.” Grabbing his phone quickly, he checked his email. He looked at me with confusion before disconnecting the call and dialing a number urgently. The next few minutes were tense as we waited for an answer, but then it rang: “What is this? We never send out emails like that!”
Phishing scams have been around for a long time. They are often used to steal personal information, like login credentials and credit card numbers from unsuspecting recipients. The scammers will send an email or message that looks like it is coming from a trustworthy entity in order to trick the victim into clicking on a malicious link, which can lead to malware being installed, the system getting frozen as part of a ransomware attack, or sensitive information being revealed. In this post, we will discuss what phishing is and the unfortunate reason why these types of attacks continue happening.
What is Social Engineering?
Social engineering is a form of hacking that focuses on deceiving individuals in order to obtain information such as login credentials and credit card numbers. The phishing attack is one example of social engineering, but there are several other types including dumpster diving, tailgating (also known as piggybacking), baiting, and whaling. Dumpster divers look through trash for important documents like bank statements or insurance details which can be used by scammers when carrying out identity theft attacks. Tailgaters try to get the victim’s attention before following them into their building so they don’t have to use an access card or code at the door. When it comes to baiting, this type of scam involves a fake email offering something valuable like money in order to entice the recipient into clicking a malicious link. Whaling targets high-profile individuals such as CEOs and other people in power who can be tricked into revealing sensitive information.
What is Phishing?
A phishing attack is a type of social engineering trick where an attacker, masquerading as a trusted entity, dupes the recipient into clicking on a link or opening an email attachment. The message appears to come from another person or company and requests information like login credentials for bank accounts, credit card numbers, and other sensitive data. By gathering this information from unsuspecting users, the scammers are able to steal or destroy their data.
How is Phishing Done?
Phishing attacks can be done through a variety of methods. The most common is through email, where the recipients are sent an unsolicited message that contains malicious links or attachments that will install malware on their computer if opened. They may also send messages claiming to offer free services like lottery winnings and asking for personal information in exchange. These types of scams often use fake social media profiles as well as websites designed to look legitimate but actually contain code with viruses embedded into them.
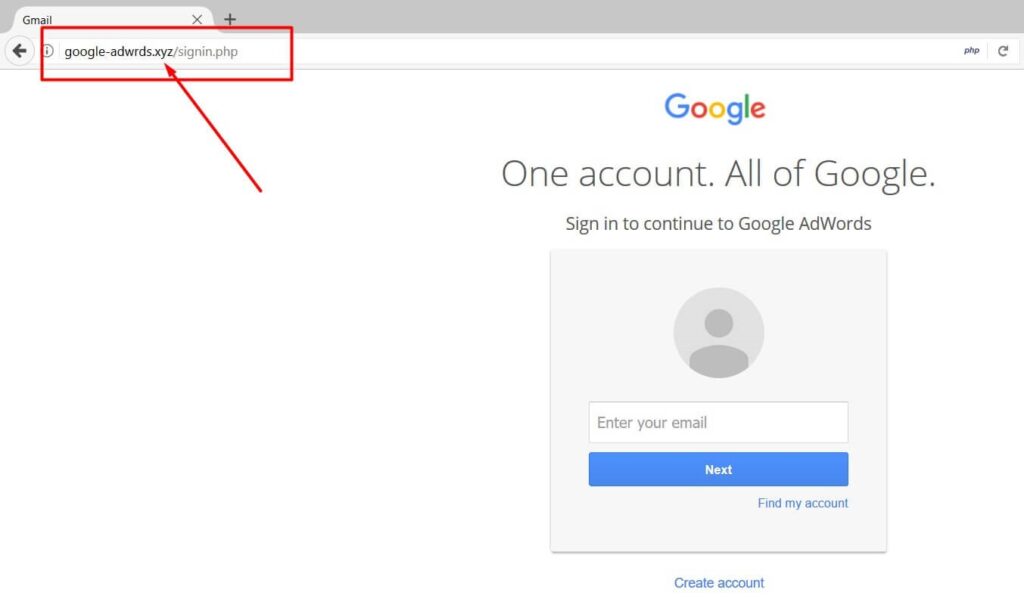
Phishing using Fake Login Page
One of the latest phishing techniques to gain popularity is using a fake login page. Hackers create web pages that look like the website you are trying to log into but actually contain malicious code that sends your data back to them when you enter it in their fields.
Phishers may also use JavaScript redirects which means they don’t even need to create fake websites as this type of attack can be carried out by embedding codes into emails, DMs, and instant messages.
Phishing attacks can occur through several different methods. The most common is spam emails, where the recipients are sent an unsolicited message that contains malicious links or attachments that will install malware on their computer if opened.
They may also send messages claiming to offer free services like lottery winnings and asking for personal information in exchange. These types of scams often use fake social media profiles as well as websites designed to look legitimate but actually contain code with viruses embedded into them.
SMS
Phishing through SMS messages is becoming an increasing trend. The attackers send mass text messages claiming to be from a bank or the government and asking for account information like usernames, passwords, PINs, credit card numbers, etc. Even if the message appears legitimate it can still contain malicious links that lead you to websites designed to look exactly like your bank’s site but are actually fakes created by hackers with the intention of stealing personal data.
How do I Know if an Email or Message Is Phishing?
There are several things you should look for in order to determine whether an email message or social media post is legitimate: – Does the sender have a personal connection with you? If not then there’s probably no reason why they should be contacting you. – Does the message contain a request for personal or financial information? If so then it’s likely to be phishing since almost all banks and businesses will never ask for this type of data over email, DMs or instant messages.
Phishing scams are increasing in volume and becoming more targeted with users; however, there is no reason to be a victim. Always keep your wits about you when clicking on links or opening DMs from people you don’t know as it can have serious consequences for your finances, safety and privacy if not careful.
– Is there broken English in the email? Phishers often don’t speak perfect English which is an easy way to determine that their messages are not legitimate ones from other people or companies. – Are there spelling errors within the text? Since good grammar and correct spelling are important when creating professional correspondence it makes sense that hackers might have trouble with these skills as well if trying to mimic another company’s emails etc.
– Is the message asking me to click on something? There’s never an instance where this would happen so just ignore any requests like these.- Have I received similar messages before but from different senders? If so then they could all be related spam attacks being carried out by hackers using one system which means that every time you open them malware gets installed onto your computer leading to further problems down the line. Am I able to verify whether the message is legitimate? If not then it’s likely to be a scam so just delete the content and ensure you don’t click on any links included within the text.
What can I do?
It’s important to be vigilant when it comes to protecting your data against phishing attacks because once you’ve clicked a bad link and given away login credentials or other sensitive info, there isn’t much you can do besides change all of your password accounts immediately before further damage is done. It’s also a good idea to be careful about the sites you visit online because many phishing pages are designed to look legitimate but actually contain code that can harm your computer.
While it may not be possible to prevent all social engineering scams, there are some steps you can take in order to protect yourself from highly targeted attacks like whaling and spam email scams which often use personalized messages with malicious links or attachments. In addition, always check up on URLs before clicking them as well as watch out for typos since scammers will purposely misspell words in their messages so they appear genuine even though they’re fake. And remember- if something sounds too good to be true, then most likely it is!
What Dangers are Associated With Phishing?
There are several dangers associated with phishing including identity theft, stolen login credentials, ransomware infections, online banking fraud, and more. Since scammers can gain access to victims’ sensitive data such as credit card numbers when they open a malicious email or click on an infected link, there’s always the risk of their personal information being stolen and used to drain bank accounts.
Phishing emails often contain links that download malware onto users’ computers which can result in them having their systems frozen as part of ransomware attacks where they are asked to pay money for it to be released again. Even if people don’t give up financial data when tricked by phishers, this type of scam can still cost victims dearly with online banking frauds, leading to losses from fake transactions done using login credentials obtained through social engineering tricks.
There are a number of reasons why phishing scams continue to happen:
- The internet is an anonymous place – It’s unlikely that people will be caught and punished for attempting to carry out these types of attacks. Without real consequences, there is little disincentive for them to continue.
- Phishing is easy and inexpensive – A number of programs can automate the process, making it even easier to target a large group of people at once.
- People want something for nothing – Many phishing attacks are done under false pretenses, like asking users to provide their login credentials in order to receive a free gift.
- Phishing attacks are difficult to protect against – The messages can appear legitimate and it is often too late for the recipient when they realize what’s happening.
Conclusion
In this post, we discussed phishing and why these types of social engineering scams continue to happen despite their dangers. We also looked at some of the reasons that make them easy to carry out in the first place, as well as how a number of programs are used to automate this process so scammers don’t have to do all the work themselves. Finally, we touched on why people want something for nothing even if there may be real consequences down the line and suggested some tips on how companies or individuals can protect themselves from falling victim to a phishing attack in