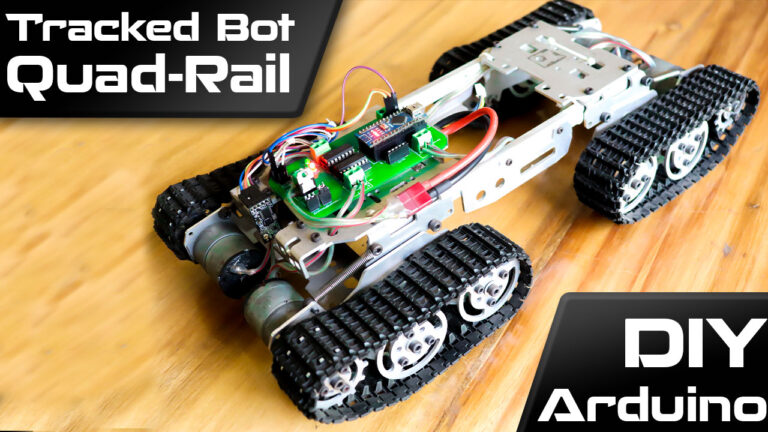
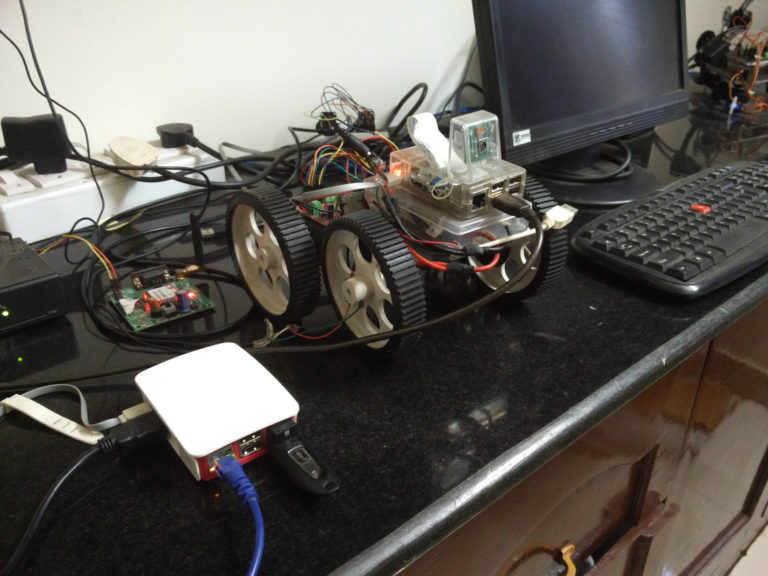
Arduino Tracked Robot using HC12 Wireless Module
Remote Controlled Tank This time I have a rough Terrain Robot with 4 Wheel Drive and dedicated suspension for it to travel over rough terrain. Check it out. Why not build one for yourself? Here we will learn how to build an Off-Road Wireless Multipurpose 4 Wheel Drive Arduino Tracked Robot for a smooth ride over rough…